 Information Resource Guide |
 Information Resource Guide |
If you suspect or have been notified that your computer system has been or is under attack, you must determine:
CIAC has collected and developed techniques to discover traces of an attack. Almost all attacks leave detectable remnants that may be uncovered and used in an investigation.
This section contains step-by-step
instructions to follow if you are investigating an actual security incident.
It can also be used as a tutorial in general techniques for use if an attack
occurs.
| This guide
helps you with
these security scenarios... |
By providing
you with
detailed information on these topics... |
| A person’s
system is linked to the
Internet; there is "a feeling" that something is wrong. A security problem might exist, but you can’t be sure. You are notified by CIAC that someone from another site that had an intruder found your site’s name in an intruder’s log file. You know that an intruder has at least "touched" your system. The extent of the contact is unknown. An incident response team informs you that an intruder was located, and the team’s log files indicate the intruder came from your site. finding the footprints left by an intruder You get a call that someone is performing an illegal action (either breaking into another system, or breaking into that particular system) right NOW. Action must be swift in order to minimize damage. You suspect you have a sniffer on your system, but don’t have the slightest idea where to start looking for it. |
displaying the users logged in to your system displaying active processes detecting a sniffer finding files and other intrusions left by an intruder |
10.1 Displaying the Users Logged in to Your System
If you suspect that there is an active intruder on your system, first determine where they are and what they are doing. This section shows you how to use these commands to find out who is on your system:
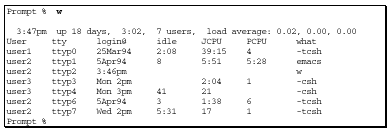 The
"w" command gives you a general overview of all users and their active
programs on the system. A sample output is shown here.
The
"w" command gives you a general overview of all users and their active
programs on the system. A sample output is shown here.
The first line displayed, the status line, gives general information: the present time, how long the system has been running, and the load on the system for various periods of time. The rest of the output from the "w" command shows you who is currently logged in to the system, which TTY they are using, and what each user is currently doing.
What to Look For
Verify that:
The output listing from the "w"
command can be easily modified to hide a skilled intruder’s existence on
the system.
Another command that displays who is on the system is the "finger" command.
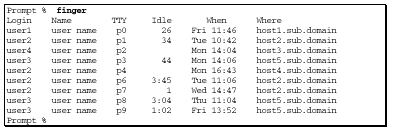 A
sample output is shown here. The "finger" command shows you who is currently
logged in to the system, which TTY they are using, the time they logged
in, and where they are logged in from.
A
sample output is shown here. The "finger" command shows you who is currently
logged in to the system, which TTY they are using, the time they logged
in, and where they are logged in from.
What to Look For
Verify that:
The output from the "finger" command can easily be modified to hide a skilled intruder’s existence.
The "who" command lists information about the users currently on the system.
This information is retrieved from the /etc/utmp file. A sample output is shown
here. This command lists who is currently logged in to the system, which TTY they
are using, login time, and where they are logged in from.
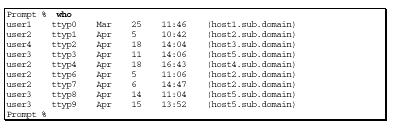
What to Look For
Verify that:
The output from the "who" command can easily be modified to hide a skilled intruder’s existence, as the command gets its information from the /etc/utmp file.
10.2 Displaying Active Processes
Even if an intruder is no longer logged in to a (potentially) penetrated system, a process may have been left running by the intruder to continue performing tasks. This section shows you how to use these commands to display the active processes running on your system:
the "ps" command
the "crash" command
The "ps -agux" command lists the processes that are executing on your system.
The command’s "a" parameter displays all processes running on the system, not just those owned by you. The command’s "g" parameter displays all processes, as opposed to those which "ps" decides are simply "interesting" (refer to the "ps" man page for the definition of "interesting").
The "u" parameter displays user-oriented output. The "x" parameter includes processes without control terminals.
The "ps" command is a reliable way to see what programs are being executed on the system. A shortened sample output is shown here.
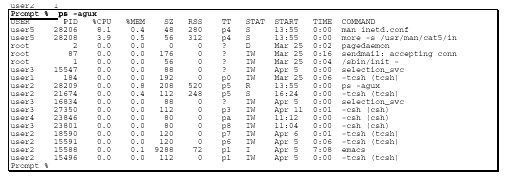
What to Look For
The following may indicate undesired activity:
In some cases, compromised systems have been found to contain a Trojaned version of "ps" which does not display intruder processes. Also, if an invalid process is running but has a valid process name, it may be difficult to distinguish the suspicious process. For example, intruders
often run sniffer processes under names such as "sendmail" or "inetd".
You can use the "crash" command to list all processes. This functions as a
cross-check against the "ps" command. That is, finding a process with "crash"
output that does not appear in "ps" output (matching pids). Once you execute
"crash," you will receive a ">" prompt. Type proc in response and quit when
you are finished running "crash".
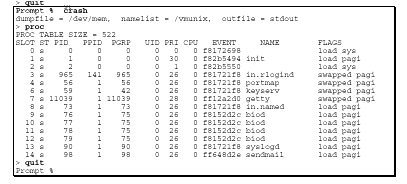
What to Look For
The following may indicate undesired activity:
Names can be faked. Like any command, "crash" can be Trojaned.
10.3 Finding the Footprints Left by an Intruder
If you suspect that an intruder has been on your system but is gone, use the commands and files described in this section to find the "footprints" the intruder may have left behind. This section shows you how to use these commands and files:
the "last" command
the "lastcomm" command
the "/var/log/syslog" file
the "netstat" command
The "last" command displays information about logins and logouts on the system from the /var/adm/wtmp file. If you can determine the username the intruder used to log in, this command can show you how long the intruder was logged in and where they logged in from. The command’s "-n" parameter is used to display the last n entries in the /var/adm/wtmp file.
A sample output is shown here.
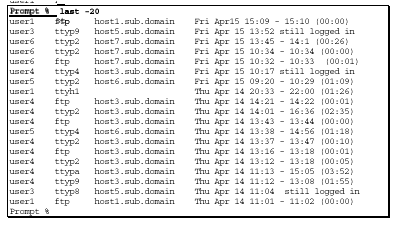
The first column contains the username, followed by the terminal device the user is connected to. If the connection used a network device, the name of a remote system is displayed in the next column. For serial devices such as dial-up modems, the column will be blank. This is followed by the login and logout time and an indication of the length of the session.
What to Look For
Vulnerabilities
An intruder who breaks into a system
can hide their tracks by deleting or modifying the /var/adm/wtmp file.
The "lastcomm" command displays the last commands executed. This command is only available if you have process accounting turned on. With this command, you can see every command issued by anyone on the system. A sample output is shown here.
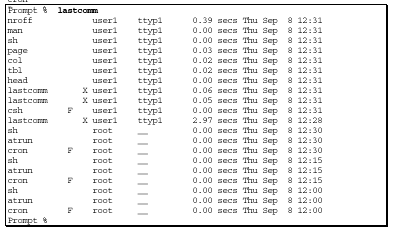
What to Look For
This command is an excellent way of seeing what a user did while on your system because it lists all commands executed by all users.
Vulnerabilities
This command produces a file that tends to get quite large very quickly as it saves the data needed to track the commands issued by every user. You should periodically rename it so that you can manage smaller files.
The "lastcomm" command only tracks the command that ran a program, but not what actions were taken after the program started (for example, it may show the editor being run, but not which files were opened after the initialization of the editor).
Many times, attacks are not discovered until days after the actual event. And in these cases, the accounting logs may have been purged by the time the attack is discovered. The biggest potential intruder-style vulnerability is that the data is kept in the file /var/adm/pacct, which the intruder can
easily delete and perhaps modify
if the proper privileges are obtained.
10.3.2 The /var/log/ syslog File
The /var/log/syslog file is a file that contains messages relating to various types of connections to your system. The content of this file is defined by the /etc/syslog.conf file. The results of this command contain extremely long lines; a shortened sample of this file is shown here.
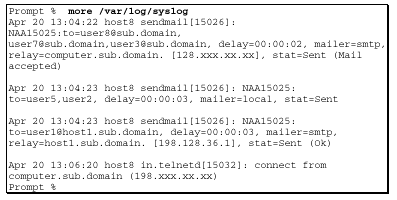
Most messages are from the sendmail program, and display the status of messages sent and received by your system. This file may also contain in.telnetd connection messages and other previously defined messages.
What to Look For
Since this file saves data on incoming as well as outgoing information, especially sendmail information, one of the things to look for is outbound E-mail to suspicious hosts. This may indicate that an intruder sent out information from your system to a remote system.
Telnet connections, both incoming and outgoing, should be examined. A short file may be suspicious, as it may indicate that this file has been edited or deleted. A ‘hole’ in the file
(a large chunk of time when no messages occur) may indicate that an intruder deleted the messages related to their time on the system. Note that this ‘hole’ may be useful in tracking down when the intruder used the system. In general, look for things that may appear out of the ordinary.
Vulnerabilities
In many cases, the /var/log/syslog file is world writable and must remain so for operational reasons. Therefore, its data may be suspect and untrustworthy.
This file tends to be very long.
Investigating all connections, especially sendmail messages, can be difficult.
This is because at least one line is written to the /var/log/syslog file
for each mail message. In addition, users tend to delete messages and forget
exactly who sent them the messages, when they were received, and what they
were about.
10.3.3 The /var/adm/ messages File
The /var/adm/messages file usually contains a listing of all messages that are
sent to the console. The actual content of this file is defined in the
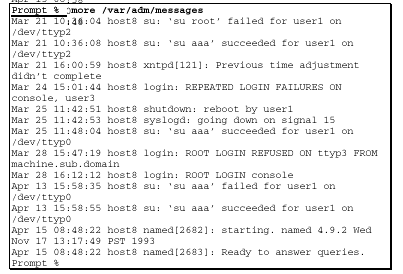 /etc/syslog.conf
file. A sample of this file is shown here.
/etc/syslog.conf
file. A sample of this file is shown here.
What to Look For
The following may indicate undesired activity:
Vulnerabilities
Once an intruder obtains root access,
this file can be modified or deleted quite easily. Also, if the syslog.conf
file is compromised, logging to this file may be discontinued.
The "netstat" command displays listening and connected processes. You should compare the output from this command with the output from the "last -n" command.
The command’s "-a" parameter is used to display the status of all sockets.
A sample output is shown here.
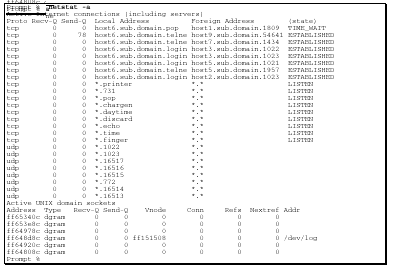
What to Look For
The following may indicate undesired activity:
In some cases, compromised systems have been found to contain a Trojaned version of "netstat" that does not show connections to or from the source of the intrusion.
Sniffers are a major source of contemporary
attacks. This section shows you how to use the "ifconfig" command to determine
if a sniffer has been installed.
The "ifconfig" command displays the current configuration of your network interface. Most Ethernet adaptors are (and should be) configured to accept only messages intended for themselves. An attacker must set a computer’s adaptor to "promiscuous mode," in order to listen to (and record) everything on its segment of the Ethernet.
A sample output of a system in promiscuous mode is shown here.
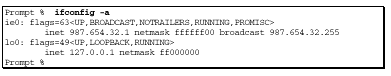 Note
"PROMISC" is the last parameter of the flag’s description.
Note
"PROMISC" is the last parameter of the flag’s description.
What to Look For
In conjunction with positive results from the above command, the following may indicate undesired activity:
Like any command, "ifconfig" can be Trojaned. If you suspect that a sniffer has been installed, obtain "cpm" from CIAC or CERT and run it. The cpm tool will test the network interface directly and report if it is in promiscuous mode.
10.5 Finding Files and Other Evidence Left by an Intruder
When an intruder breaks into a system, information related to the attack is occasionally left behind. This information includes, but is not limited to directories, shell scripts, programs, and text files.
This section describes various files that have been found on compromised systems. Because file names can be easily changed, the actual name of the file may be different than the file names listed in this section. Many times, intruders try to hide files; methods for achieving and detecting this will be also be described.
What to Look For
When you look for files left behind by an intruder, you should:
Obtaining a Baseline of What Your Normal Operating System Looks Like To obtain a baseline of your normal operating system, you should periodically run the commands described in this document. Record and become familiar with the output from these commands. Also, obtain and periodically use SPI and Tripwire.
Finding Files and File and Directory Names Commonly Used by Intruders The file names given in this section are commonly used by intruders. Start by looking for these file names, but realize that, as intruders learn that their bogus file names are discovered, they will change them. You must ultimately look for a name or names that do not belong.
Suspicious Files
Often, the best indication of whether or not a system has been compromised comes from a thorough examination of its file systems. The creation or modification of files is often a strong indication of intruder activity on a system. Occasionally, the intruder will modify ("Trojan") system
programs to hide the intrusion. Some system administrators have discovered that a command such as "ps" will be Trojaned to ignore the intruder’s processes. Keep this in mind when running any command, because if a command has been Trojaned, the results of the command will be questionable.
![]()
The "find" command, run preferably as root, will list all files that have been modified in the previous n days: Note that many intruders routinely change file modification times to hide changes made to the system. Many of these modifications may still be detected by examining a file’s inode change time, which is more difficult for an intruder to forge. The following command will locate all files with inode change times that have changed in the last n days:
![]() While
examining the results generated by the above commands, consider the hidden
files and directories often used by attackers described in the next section,
"Hidden Files and Directories."
While
examining the results generated by the above commands, consider the hidden
files and directories often used by attackers described in the next section,
"Hidden Files and Directories."
Hidden Files and Directories
Intruders often attempt to conceal their presence on a system by using hidden files or directories; that is, those with names that begin with a "." (period). They are not displayed by the "ls" command, unless the "-a" parameter is used. The following names are commonly used by intruders:
In many cases, intruders use compromised hosts to store and crack password files from other systems. Finding files that contain password entries from other systems or finding password cracking software (such as Crack) probably indicates intruder activity on your system.
Setuid Files
Unix systems allow users to temporarily elevate their privileges through a mechanism called setuid. When a file with the setuid attribute is executed by a user, the program is given the effective access rights of the owner of the file. For example, the "login" program is typically a setuid file owned by root. When a user invokes "login", the program is able to access the system with super-user privileges instead of the user’s normal privileges. Intruders often create setuid files that enable them to quickly gain root access during later visits to the system. Often, the file is placed in a hidden directory or has a hidden filename (e.g., ".sh"). Setuid files appear in directory lists with an "s" in place of the "x" in the execute bit position. For example, the output of the "ls -l .sh" command would display output similar to the following:
![]()
Note that a typical Unix system contains dozens of legitimate setuid programs necessary for normal operation of the system. Setuid files that should be suspected include:
![]()
All Unix systems provide some level of accounting, recording the actions of both users and system processes. The amount of information recorded can vary significantly depending on both the version of Unix and its configuration. The default for many systems is to record little more than login/logout times for users. At the other end of the spectrum, systems running at an Orange Book C2 level of assurance can easily generate several megabytes of log information per hour.
To detect an intrusion, begin by examining whatever logs are available on your system. Bear in mind, however, that if an intruder gained access to your system, the information stored in the logs may have been modified to hide the intruder’s tracks. Use the "last" and/or "lastcomm" commands discussed in the next two sections (and previously described above) to help you examine the logs.
The "last" Command
The "last" command, available on almost every version of Unix, displays login and logout activity for the system. This can be a useful place to begin an investigation. Check the login times and locations for all users and compare them to expected norms. Refer to the previous discussion of the "last" command for more information and a sample output.
The "lastcomm" Command (Accounting)
On systems with process level accounting enabled, the "lastcomm" command will generate a detailed list of all commands executed by each user on the system. Unusual or inappropriate system activity can often be discovered in the results from this command. For example, "lastcomm" output indicating repeated executions of the "tftp" program might indicate attempts to steal password files using TFTP. For information on enabling process accounting on a specific Unix system, refer to the man page for "acct". Refer to the previous discussion of the "lastcomm" command for more information and a sample output.
Many system process events generate messages. For example, the "su" utility often makes a log entry when a user attempts to become the "super-user." These messages may prove useful in discovering unusual activity possibly caused by an intruder.
These messages are often archived in log files for later examination. Commonly used files include /var/log/syslog and /var/adm/messages; however, the file names may vary from system to system. Refer to the sections about these files in this guide or to the man page for "syslog" for more information.
~/.history
Some shells, tcsh for example, keep a record of the most recently executed commands for each user. This information is usually stored in a file in the user’s home directory and is often called ".history". Examining this file may allow the reconstruction of the recent activities of a specific user.
Inspecting Processes Look for:
Inspecting Targeted Files
/etc/passwd
Look for:
The ~/.forward file is used to manipulate E-mail forwarding. When examining this file, look for any
suspicious entries (that is, would it make sense for a legitimate user to manipulate his or her E-mail in that manner?).
~/.rhosts and hosts.equiv
The ~/.rhosts file can be used to allow remote access to a system and is sometimes used by intruders to create easy backdoors into a system. If this file has recently been modified, examine it for evidence of tampering. Initially and periodically verify that the remote host and user names
in the files are consistent with local user access requirements. View with extreme caution a "+" entry; this allows users from any host to access the local system.
An older vulnerability is systems set up with a single "+" in the /etc/hosts.equiv file. This allows any other system to log in to your system. The "+" should be replaced with specific system names. Note, however, that an intruder cannot gain root access through /etc/rhosts entries.
~/ftp Files
Directories which can be written to by anonymous FTP users are commonly used for storing and exchanging intruder files. Do not allow the user "ftp" to own any directories or files.
System Executables in User Directories
Copies of what may appear to be system executables in user directories may actually be an attempt to conceal malicious software. For example, recent attacks have made use of binaries called "vi" and "sed", two commonly used Unix utilities. However, these particular binaries were actually renamed intrusion software files, designed to scan systems for weaknesses.
![]() System
binaries found in unusual locations may be compared to the actual executable
using the "cmp" command:
System
binaries found in unusual locations may be compared to the actual executable
using the "cmp" command:
Determining if System Executables Have Been Trojaned SPI or Tripwire must be set up before an exposure in order to determine if your system executables have been Trojaned.
Use your CD-ROM to make sure you have a good copy of all your system executables, then run the above mentioned products according to the instructions that accompany them to create a basis for later comparison. Periodically, run SPI or Tripwire to detect any modification of the system executables.
/etc/inetd.conf
Print a baseline listing of this file for comparison. Look for new services.
/etc/aliases
Look for unusual aliases and those that redirect E-mail to unlikely places. Look for suspicious commands.
cron
Look for new entries in cron tab, especially root’s. Look at each user’s table.
/etc/rc*
Look for additions to install or reinstall backdoors or sniffer programs. Use SPI or Tripwire to detect changes to files.
NFS Exports
Use the "showmount -a" command to find users that have file systems mounted.
Check the /etc/exports (or equivalent) file for modifications. Run SPI or Tripwire to detect changes.
Changes to Critical Binaries
Run SPI or Tripwire initially and then periodically. Use the "ls -lc" command to determine if there have been inappropriate changes to these files.
Note that the change time displayed by the "ls -lc" command can be changed and the command itself can be Trojaned.
Section References:
Pichnarczyk, Karen, Weeber, Steve
& Feingold, Richard. "Unix Incident Guide: How to Detect an Intrusion
CIAC-2305 R.1". C I A C Department of Energy. December, 1994.
Appendix A : How Most Firewalls are Configured
All firewalls from any vendor that will be providing Internet firewall facilities require a routed connection to the Internet to provide traffic flow between the Internet and in-house network facilities. There are usually more than one router involved in such connections. With some effort, connections are successful but usually difficult to monitor and manage.
A typical set-up with an Internet Service Provider where a firewall is configured in the network is set-up as follows:
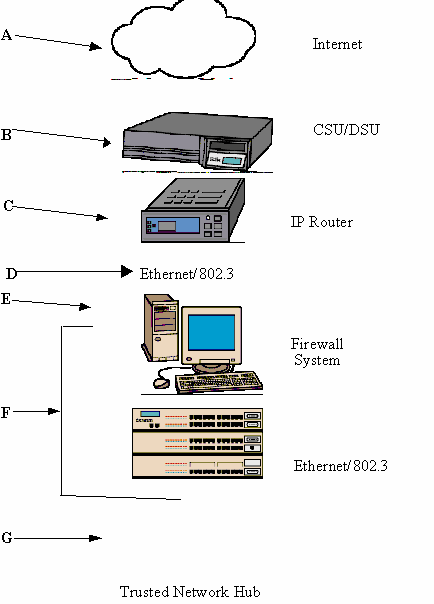
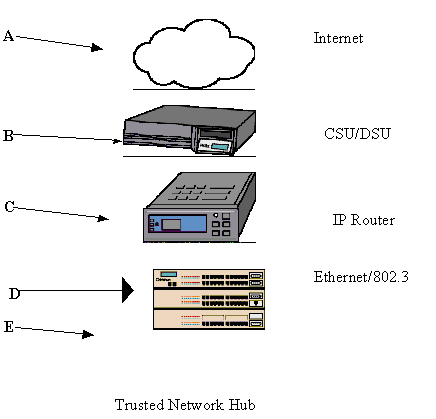
In the above diagram, the network and firewall connection parts are as follows:
b) A CSU/DSU interface to the telephone drop from the local equipment company (LEC)
c) A router system to connect to the ISP’s router connection to the Internet
d) An Ethernet/802.3 or Token Ring/802.5 UTP connection from the router to the firewall
e) A "dual-homed gateway" firewall system with two LAN controllers (in this diagram, two Ethernet/802.3 connections are provided)
f) An Ethernet/802.3 UTP connection from the firewall to the internal network
g) An internal network configuration. In this case, a simple stacked hub architecture (e.g. Cabletron Mini-MAC)
One of the more popular configurations of a "firewall" is to use an external router as the singular security facility between an untrusted network (e.g. Internet) and the internal, trusted network. This configuration is called a "screening router" set-up. A typical configuration is as follows:
The network configuration for a "screening router" is as follows:
b) A CSU/DSU interface to the telephone drop from the local equipment company (LEC)
c) A router system to connect to the ISP’s router connection to the Internet. On this router, there are a variety of "filter" rules, which provide some level of security between the trusted internal network and the untrusted Internet connection.
d) An Ethernet/802.3 or Token Ring/802.5 UTP connection from the router to the internal network
e) An internal network configuration. In this case, a simple stacked hub architecture (e.g. Cabletron Mini-MAC)
Appendix B: Basic Cost Factors of Firewall Ownership
The following 20 base factors comprise the basic costing issues in the ownership of firewall products:
Appendix C: Glossary of firewall related terms
Appendix D: Top 10 Security Threats
1. Firewall and System Probing
Hackers are using sophisticated, automated tools to scan for vulnerabilities of a company's corporate firewall and systems behind the firewall. These hacker tools have proved to be quite effective, with the average computer scan taking less than three minutes to identify and compromise security.
Companies can prevent this by ensuring that their systems sit behind a network firewall and any services available through this firewall are carefully monitored for potential security exposures.
2. Network File Systems (NFS) Application Attacks
Hackers attempt to exploit well-known vulnerabilities in the Network File System application, which is used to share files between systems. These attacks, usually through network firewalls, can result in compromised administrator access.
To combat this, ensure systems do not allow NFS through the firewall, and enable NFS protections to restrict who can access files.
3. Electronic Mail Attacks
Hackers can compromise network systems by simply sending an e-mail to it. Companies who accept e-mail from the Internet and who have exposed versions of the sendmail program are potential targets from this attack. Last year more than 20,000 systems were compromised due to this exposure.
To prevent this from occurring, check with vendors to ensure systems are running a correct version of sendmail or some more secure mail product.
4. Vendor Default Password Attacks
Systems of all types come with vendor-installed usernames and passwords. Hackers are well educated on these default usernames and passwords and use these accounts to gain unauthorized administrative access to systems.
Protect systems by ensuring that
all vendor passwords have been changed.
5. Spoofing, Sniffing, Fragmentation and Splicing Attacks
Recently computer hackers have been using sophisticated techniques and tools at their disposal to identify and expose vulnerabilities on Internet networks. These tools and techniques can be used to capture names and passwords, as well as compromise-trusted systems through the firewall.
To protect systems from this
type of attack, check with computer and firewall vendors to identify possible
security precautions.
6. Social Engineering Attacks
Hackers will attempt to gain sensitive or confidential information from companies by placing calls to employees and pretending to be another employee. These types of attacks can be effective in gaining usernames and passwords as well as other sensitive information.
Train employees to use a "call-back" procedure to verify the distribution of any sensitive information over the telephone.
7. Easy-To-Guess Password Compromise
Most passwords that are easy to remember are also easy to guess. These include words in the dictionary, common names, slang words, song titles, etc. Computer hackers will attempt to gain access to systems using these easy-to-guess passwords usually via automated attacks.
Protect systems by ensuring that passwords are not easy to guess, that they are at least eight characters long, contain special characters and utilize both uppercase and lowercase characters.
8. Destructive Computer Viruses
Computer viruses can infect systems on a widespread basis in a very short period. These viruses can be responsible for erasing system data.
Protect systems from computer viruses by using anti-virus software to detect and remove computer viruses.
9. Prefix Scanning
Computer hackers will be scanning company telephone numbers looking for modem lines, which they can use to gain access to internal systems. These modem lines bypass network firewalls and usually bypass most security policies. These "backdoors" can easily be used to compromise internal systems.
Protect against this intrusion by ensuring modems are protected from brute force attacks. Place these modems behind firewalls; make use of one-time passwords; or have these modems disabled.
10. Trojan Horses
Hackers will install "backdoor" or "Trojan Horse" programs on businesses computer systems, allowing for unrestricted access into internal systems, which will bypass security monitoring and auditing policies.
Conduct regular security analysis
audits to identify potential security vulnerabilities and to identify security
exposures.
|
|
|
|
|
| Boink (similar to Bonk, Teardrop and New Tear/Tear2), a hack | System seizure | Bad fragment attack | Sends bad packet fragments that cannot be correctly reassembled, causing the system to fail |
| DoS (Denial of Service) | Lack of access to resources and services | Denial of Service attacks tie up system resources doing things you do not want so you cannot get service | Examples include floods (which soak up bandwidth and CPU) and disconnects (which prevent you from reaching hosts or networks) |
| Floods (Nukes), a DoS attack | n/a | Large amounts of ICMP (usually) or UDP useless packets | Ties up system by making it respond to floods of useless garbage |
| ICMP flooding (flood ping), a DoS attack | Loss of bandwidth (slow responses from the Internet) and poor response time on the desktop | A flood of ICMP (ping) requests that tie your system in knots responding to garbage traffic. This is analogous to wasting your time answering the door to never-ending doorbells that do nothing. | Ties up CPU time and wastes your bandwidth with the garbage traffic. For example, "Pingexploit" typically attacks Unix systems with oversized ICMP packet fragments. |
| Identification flooding (Identd), a DoS attack | Loss of bandwidth (slow responses from the Internet) and poor response time on the desktop | Similar to an ICMP flood, but requests information from your system (TCP port 113) | Very often slows the CPU down (even more than an ICMP flood) since identification responses take more time than ICMP responses to generate |
| Jolt (SSping, IceNuke), a hack | System seizure | Oversized, fragmented packet which causes the system to seize up | System stops working and must be rebooted |
| Land, a hack | System seizure forcing cold reboot | Spoofing attempt which establishes TCP/IP connection to you from you. This SYN request forces the system to connect to itself, thereby locking itself up. | The attacked system attempts to connect to itself and seizes up |
| Hack | N/A | An application or a packet that exploits a weakness in operating system, application or protocol | Varied results. Examples include smurf, teardrop, land, newtear, puke, ssping, jolt, etc. |
| Pong, a hack | Loss of bandwidth (slow responses from the Internet) and poor response time on the desktop | Flood of spoofed ICMP packets, usually changing the spoofed source address with every packet | Reboot to solve |
| Puke, a hack | Disconnection from a server (usually IRC) | Spoofs an ICMP unreachable error to a target. This forces a disconnect from a server. | Usually preceded by an ICMP port scan where "pings" are sent to a system to find a vulnerable port being used to connect to a server |
| Scan, a generic technique and a DoS attack | System slows | A progressive, systematic testing of ports for an "opening." This attack can chew into system resources since its target is usually changing. It often requires a proper firewall or large, multi-port block to prevent. | Usually used prior to a hack to find a vulnerable attack spot. This is considered a brutish form of attack and is not as effective as other floods for tying up resources. It usually precedes a more "elegant" attack form. |
| Smurf, a hack | A very effective CPU crushing flood-like attack. Apparent system seizure. | Spoofs ICMP packets requesting a response and triggering multiple responses | A form of flood that is very dangerous since it can get a "many-for-one" effect, tying up lots of CPU cycles for relatively few packets sent |
| Spoofing (IPspoof) | N/A | An attack masking style that makes traffic appear to come from a legitimate target or that attempts to frame innocent bystanders for attacks for which they are not responsible | Particularly nasty attack because hacks, floods and nukes are illegal in most countries and subject to prosecution |
| unreachable (dest_unreach)- a DoS attack | "Destination Unreachable" messages and disconnection from a server | There are 2 forms of this—client unreachable and server unreachable. The server unreachable attack sends an ICMP message to the system fooling it into thinking its traffic can no longer reach the server, so it gives up. The client unreachable form does the same thing to the server with respect to your system. | |
| WinNuke, a hack and a DoS attack, but not a flood | Loss of networking resources | Sends OOB (Out-of-Band) data to port 139 and exploits Win 3.11, Win95, Win NT 3.51 and Win NT 4.0 systems | Does not crash the system, but it causes a fatal exception requiring a reboot to regain TCP/IP (Internet) connectivity |
Appendix F: Top 10 Security Precautions
1. Firewall Sensitive Systems
Ensure corporate systems are protected from Internet attacks. Deploy a firewall between these systems and the Internet to guard against network scans and intrusions.
2. Obtain Security Alert Information
Subscribe to security alert mailing lists to identify potential security exposures before they become problems. CERT (Computer Emergency Response Team at Carnegie Mellon University) is a good place to start. The URL for CERT's Web site is cert-advisory-request@cert.org. The e-mail address is cert@cert.org.
3. Review System Audit Trails Regularly
Regularly check logging data and audit trails to look for unusual or suspicious activity.
4. Backup Data
Don't be a victim of accidental or malicious data erasure. Backup all sensitive data on a regular basis.
5. Purchase and Deploy Anti-Virus Software
Computer viruses can spread throughout a system in minutes. Check systems for viruses on a regular basis.
6. Change Passwords On A Regular Rotational Basis
Don't pick easy to remember passwords and change them often. Consider the use of one-time password tokens to avoid password compromise threats.
7. Deploy Vendor Security Patches
Consult with vendors and obtain any system security patches that can be used to add additional layers of protection.
8. Establish and Enforce A Security Policy
Develop and enforce a company-wide computer and physical security policy.
9. Employee Awareness
Ensure all employees and management
are briefed regularly on security threats, policies, corrective measures
and incident reporting procedures.
10. Make Use Of Public Domain Security Tools
A variety of public domain security tools exist on the Internet, many of which can be used to assist in the protection of computer systems.
Back Door: An entry to a program, or system created by its designer to allow special access; often without proper security checks. A classic back door was used by a teen-age hacker in the movie "War Games".
Bacterium: A program which spreads to other users or systems by copying itself as a by product of execution. It doesn't infect other programs, but acts independently.
Bogus Programs: Programs which do not do what they have been advertised to do. A example is XTRATANK, which claims to double your hard drive space. It merely diddles the file allocation to double the reported size of the disk.
Boot Sector Virus: A virus secreted in the boot sector or replacing the boot sector on a floppy disk. Also a virus on the master boot block of a hard disk, or in the partition table of a hard disk. N.B. even non-systems floppy disks still have a boot sector; they just lack the boot program on that block ! Examples are Stoned and Michelangelo viruses.
Bug: An error in the design or implementation of a program, that causes the program to do something unintended. Remember even viruses have bugs. The original "bug" was a moth stuck in a relay of ENIAC.
Checksum: a number that uniquely defines a file, block or other bit of computer code. A checksum is calculated by applying an algorithm to each byte of the code and rotating it, logically ANDing or ORing it to some standard, or otherwise encoding it. The result is a single number which is a numeric finger-print. See cyclic redundancy check (CRC).
Cracks: Programs with the anti-copying protection removed, disabled or by-passed. Both hard-ware and software anti-pirating techniques can be broken with the appropriate knowledge and software.
Cyclic Redundancy Check (CRC) - A unique numeric finger-print of a file, block or other bit of computer code. This is usually calculated using a look-up table. It is common in error checking protocols. See checksum.
Device Bomb: A program which executes based on the presence of a particular device, such as a com port, hard-drive D:, etc., usually with malicious actions.
Droppers: Programs which have a legitimate use, but contain viruses which are secretly planted in system. Droppers may actually be commercial software hacked to drop viruses.
FAT: File Allocation Tables. These areas of the formatted floppy or hard disk contain information used by the system to locate and maintain the file structure.
File Viruses: These viruses infect files with *.COM or *.EXE extensions. Friday the 13th is an example. Also included in this category are viruses which use the "corresponding files" technique. These viruses search for directories with files with .EXE extensions and then creates a file of the same name with a .COM extension. Since DOS executes files with the *.COM extension before those with the .EXE extension, the virus is executed and then passes control to the .EXE file.
Hacks: Software which has been illegally modified by a system expert. See cracks, pirates, droppers, etc.. This may be as simple as modifying parts of the code with a debugger; to patching the system to snatch interrupts.
Hoaxes: Programs which claim to do the impossible; and don't. An example is a file 2496 which claims to provide instructions on running a 2400 bps modem at 9600 or even 14400 bps. If you follow the instructions, you get a modem which runs at 0 bps.
Immunization: An anti-virus strategy to prevent virus infection. This may involve putting a virus signature into software to be immunized in hopes of fooling a virus into believing the code is already infected. It may also involve creating checksums for each file which can be compared during later anti-virus examinations to guard against virus infection.
Interrupt: A hardware or software signal which indicates to the OS some event such as a keystroke has happened. It is typically taken care of by an interrupt handler which services the event.
Jokes: Programs which do something intended to be amusing, without causing serious harm, or replicating. BUGS, which cause little bugs to run across the screen when executed is an example.
Logic bomb: A program which executes on the occurrence, or lack of occurrence of a set of system conditions. Classic examples are programs which cease functioning if the programmer's name is removed from the company's payroll list.
Multi-partite Viruses: These viruses infect both boot sectors and files. Tequila is an example.
Pirates: Any illegally obtained software. Also software which has had the copy-right notices, or other identification altered or removed.
Polymorphic Viruses: These viruses change their characteristics as they replicate. Many of these utilize the Bulgarian Dark Avenger's mutating engine. The Whale virus is an example.
Rabbit: A program designed to exhaust a system resource (e.g. CPU time, disk space, terminal I/O, etc.) by replicating itself without limit. It differs from a bacterium in that it is specifically targeted at a system resource; and from a virus in that it is a self contained program.
Rogue Program: A program that is no longer under the control of its owner, the system or its executing terminal; a.k.a. zombie. A virus is the ultimate rogue program!
Stealth Viruses: These viruses conceal the results of infection; keeping file length unchanged for example, or modifying the file in such a way that the checksum is not changed. They may simply alter the system so that the file length is reported unchanged although it is actually increased. Hundred years is an example.
Systemic Viruses: These viruses infect parts of the system other than the boot block. The file allocation table (FAT), device tables, directories, device drivers and COMMAND.COM are typical targets. Number of the Beast is an example.
Time Bomb: A logic bomb activated after a certain amount of time, or on a certain date. The classic example is a program that ceases functioning on a given date, as a control for leasing it. Such a program is often re-activated by an appropriate password.
Trojan Horse Programs: A program which has a hidden aspect which causes malicious damage. The classic is AIDS, which purports to be an AIDS data base, but actually destroys the hard disk when executed. False logon screens which snatch the users logon ID and password are another example.
Virus (pl. viruses): a program that can "infect" other software by modifying them to include a copy of itself. A program need not cause malicious damage to be a virus; the act of "infecting" other programs is central to the definition.
Worm: A program that spreads copies
of itself through-out a network. The first use of the term was applied
to a program that copied itself benignly around a network, to use otherwise
unused resources for distributed computation. A worm becomes a security
problem when it spreads against the wishes of the system owners, and disrupts
the network by overloading it.
Appendix
H: Network Terms Glossary
AAL An acronym for ATM adaptation layer, which interprets the type and format of user data messages, and then translates these messages into ATM format by packaging them into the 48-byte payload portion of an ATM cell. The AAL’s interpretation of data type and format is based on the specific class of service assigned to the data by the application. The AAL provides support for four different service classes and provides five different AAL types to accommodate a particular service class. AAL1 is used for data that require connection-oriented, constant-bit rate transmissions (e.g., voice transmissions); AAL2 is used for data that require connection-oriented variable-bit rate transmissions (e.g., a videoconferencing application); AAL3 and AAL4 are used for connection-oriented or connectionless variable-bit rate transmissions (e.g., bursty data typical of LAN applications such as those found on frame relay and SMDS networks); and AAL5, which is an improvement to AAL3, is used for transmissions in which higher layer protocols provide error recovery.
AAUI Apple Computer Corporation’s proprietary attachment unit interface (AUI). "AAUI" stands for "Apple Attachment Unit Interface."
Access Line A term used in frame relay to denote the local loop. Also called port connection.
Active Monitor A station on a token ring network that oversee the ring and ensure that it is functioning properly. Also called a monitor station.
Address A unique number assigned to a device to identify its location within a network. An address also can uniquely identify a network application process.
Addressing A network concept that describes the process of assigning unique identification numbers (called addresses) to a networked device.
ADSL An acronym for asynchronous digital subscriber line, which is a DSL variant in which traffic is transmitted at different rates in different directions. Downstream rates range from 1.5 Mbps to 9 Mbps; upstream rates range from 16 kbps to 1 Mbps. Rates depend on line quality and local loop distance. Suitable for Internet or intranet access, video-on-demand, database access, remote LAN access.
ADSL Lite A slower ADSL; also called G.lite. Downstream rates equal 1 Mbps; upstream rates equal 128 kbps. Intended primarily for homes.
Alignment Error An Ethernet/802.3
frame that does not end on a "byte-boundary."
Always On/Dynamic ISDN (AO/DI) An initiative from the Vendor’s ISDN Association (VIA) in which a portion of the D channel, which is always active and constantly connected to the provider’s switch, is used to transmit user packet data.
Ambient Noise Electrical noise that is always present and is generated primarily by transmission equipment like transmitters, receivers, and repeaters. Ambient noise also can be induced by external sources such as fluorescent light transformers, electrical facilities, and heat. Ambient noise makes it difficult for receiving equipment to distinguish between incoming signals. Also called thermal noise.
Analog Refers to any physical device or signal that varies continuously in strength or quantity over an infinite range of voltages or currents. An example is voltage in a circuit.
Analog Communication Refers to any communication method based on analog principles. In analog communications, signals flow across a wire in the form of electromagnetic waves. These waves resemble a sine curve and have the following three characteristics: amplitude, which is the level of voltage on a wire (or the intensity of a light beam when dealing with fiber-optic cable); frequency, which is the number of oscillations, or cycles, of a wave in a specified length of time; and phase, which is the point a wave has advanced within its cycle. Typically associated with voice transmission rather than data transmission because voice transmission facilities, such as the telephone, were initially analog-based.
Application Gateway Firewall See proxy server.
Application Program Software that performs a specific function such as e-mail.
Application Protocol Defines how an application is to be implemented on a network. Also includes specific user programs for interacting with an application.
ARP An acronym for address resolution protocol, which is an Internet protocol that binds a node’s IP address to its corresponding MAC sublayer (hardware) address.
Asynchronous Communication A data transmission method that requires the sending node to encapsulate special start and stop bits within each unit of data being transmitted. Thus, data can be transferred at any time by the sending node without the receiving node having any advance notification of the transfer.
ATM An acronym for asynchronous transfer mode, which is a connection-oriented, full- duplex, and point-to-point high-speed cell-switched network architecture that was created in the late 1980s/early 1990s to apply circuit switching concepts to data networks. Designed to carry data in 53-octet cells, ATM can be used to transmit data, voice and video—separately or simultaneously—over the same network path. Although not based on any specific physical layer protocol, ATM is generally carried over SONET. Also known as cell relay to distinguish it from frame relay.
Attenuation The decrease in signal strength, which occurs as the signal travels through a circuit or along a cable. The longer the cable, the greater the attenuation. Also, the higher the frequency of the signal, the greater the attenuation.
AUI A 15-pin "universal" connector that allows a device to be connected to UTP, thick or thin coax, or fiber-optic cable via an external transceiver. "AUI" stands for "attachment unit interface.
Autonomous System (AS) A collection of networks controlled by a single administrative authority, and which share a common routing strategy. Routers connecting networks within an AS trust each other and exchange routing information using a mutually agreed upon routing protocol. Also known as a routing domain or protocol area.
Auto-wrapping A term used to describe the "self healing" of a token or FDDI ring that has been cut in a single spot. The break in the active ring is corrected by establishing a loopback connection to the inactive ring. This creates a single virtual ring and allows the network to continue to function at full speed.
B Channel A 64 kbps ISDN clear channel (no signaling information is sent on the channel) used to transmit computer data (text and graphics), digitized voice, and digitized video. Most basic ISDN services are based on multiple B channels.Also called a bearer channel.
Backbone Switch A term used to describe one application of an Ethernet switch in which the switch serves as the backbone for the entire LAN. In this application, the network topology is called a "collapsed backbone."
Bandwidth In analog communications, bandwidth is the total capacity of a communications channel measured in Hertz (Hz). It is the difference between the highest and lowest frequencies capable of being carried over a channel. The greater the bandwidth, the more signals that can be carried over a given frequency range. In digital communications and networking, bandwidth is the theoretical capacity of a communications channel expressed in bits per second (bps), which is called data rate.
Baseband Cable Uses the entire bandwidth of the cable to carry a single signal.
Baud A unit of signaling speed, named after the French engineer Jean Maurice Emile Baudot (1845-1903). It is another term used to express the capacity of a channel, but is different from bits per second.
Baud Rate A measure of the number of times line conditions (i.e., frequency, amplitude, voltage, or phase) change each second. At low speeds (under 300 bps) data rate (measured in bps) and baud rate are the same because signaling methods are relatively simple. As speed increases, signaling methods become more complex. Baud rate then differs from data rate because several bits are typically encoded per baud. That is, each signal can represent more than one bit of information.
Bearer Channel See B channel.
BECN An acronym for backward explicit congestion notification, which is a one-bit field in a frame relay frame that is set to 1 by a frame relay switch to denote that a frame transmitted toward the sending node experienced congestion.
Bend Radius The radius in which cable (copper or fiber) can be curved or "bent" without breaking. Fiber is much more flexible than copper cable and can be bent in much smaller radii than equivalent copper.
B-ISDN An acronym for broadband ISDN, which is an extension of ISDN that provides full-duplex data transmission at OC-12 rates (622.08 Mbps) and is designed for delivery of interactive services (e.g., videoconferencing and video surveillance), and distribution services (e.g., cable TV and high definition TV). B-ISDN is also the basis for ATM.
Bit-Time A unit of measure equal to 0.1 µs. Thus, a one bit transmission requires 0.1 µs. Transmitting a 64-byte Ethernet/802.3 frame requires 512 bit-times or 51.2 µs.
BNC Connector A type of connector used with thin coaxial cable. There are several interpretations of BNC, including Bayonet Neill-Concelman (named after its developers), Bayonet Nut Connector, Barrel Nut Connector., and British National Connector.
BONDING An acronym for bandwidth on demand interoperability network group, which is a protocol that aggregates two ISDN B channels into a single 128 Mbps circuit.
BRI An acronym for basic rate interface, which is an ISDN basic access channel that comprises two 64 kbps B channels, one 16 kbps D channel, and 48 bits of overhead used for framing and other functions. Commonly written as 2B + D.
Bridge A layer 2 device that interconnects two or more individual LANs or LAN segments. A transparent bridge is used in Ethernet/802.3 and 802.5 (Token Ring) networks; a source routing bridge (introduced by IBM) is used exclusively in token ring networks. Bridges keep local traffic local, but forward traffic destined for a remote network. Forwarding/filtering decisions are based on MAC sublayer (i.e., hardware) addresses. Bridges partition Ethernet/802.3 networks into multiple collision domains.
Broadband Cable Shares the bandwidth of a coaxial cable among multiple signals.
Broadcast A data transmission that s destined to all hosts connected to a network. A broadcast message is a special multicast message.
Broadcast Design A network configuration that consists of nodes sharing a single communications channel. Every node connected to this shared medium "hears" each other’s transmissions.
Broadcast Storm A network phenomenon that occurs when several broadcast messages are transmitted at the same time. Broadcast storms can use up a substantial amount of network bandwidth, and in many cases, can cause a network to crash or shut down.
Brouter A combination bridge-router; a bridge with routing capabilities.
Bus Design A specific design based on a broadcast topology. All nodes are directly connected to the same communications channel.
Cable See wire.
Cable Modem A modem that uses cable television lines for data communications. These lines use broadband coaxial cable, which has a multitude of frequencies available and significantly higher bandwidth than the UTP cable used by the telcos. Cable modems provide an Ethernet/802.3 network interface that enables a computer to connect to the cable. Once connected, it is as if the PC were connected to an Ethernet/802.3 LAN. The connection is always "up," and multimegabit data rates are possible. Depending on the cable operator and service, current upstream rates fro cable modems are somewhere between 500 Kbps to 3 Mbps; downstream rates range between 10 Mbps to 30 Mbps.
Capacitance The property of a circuit that permits it to store an electrical charge. The capacitance of a cable determines its ability to carry a signal without distortion. The lower the capacitance, the longer the distance a signal can travel before signal distortion becomes unacceptable.
Carrier Sense Protocol A network protocol that requires nodes to first listen ("sense") for the "sound" of another node’s transmission prior to accessing a shared channel.
CCITT An acronym for Consultative Committee for International Telephony and Telegraphy, which was formerly an international standards organization. CCITT is now part of ITU.
CDDI An acronym for copper distributed data interface, which is an interface that provides a 100 Mbps data transmission rate over copper. A CDDI network is similar to an FDDI network. CDDI also is restricted to connections between concentrators on the ring and single attachment devices, not for the ring itself.
Cell A unit of data that is transmitted across a network. Similar to a data frame. When used in the context of ATM, a contains exactly 53-bytes—48 bytes for user data and 5 bytes for overhead.
Cells in Frames (CIF) Defines a method for transporting ATM protocols over Ethernet and token ring LANs. CIF is a LAN technology that provides LANs with ATM features including QoS and the seamless integration of data, voice, and video.
Centralized System A single computer that provides all the computing resources for all offices and departments within an organization via computer terminals that are connected to the centralized system.
Check Bits See redundancy bits.
Checksum A parameter used to detect errors. Checksums are calculated using a predetermined generator polynomial and assigned to a specific checksum field of a data frame.
CIDR An acronym for classless inter-domain routing, which allows sites to advertise multiple IPv4 Class C networks by using a single prefix.
Ciphertext A coded message. See encryption.
CIR An acronym for committed interface rate.
Circuit Gateway Firewall A device or product that involves monitoring the session set- up between a system and the user security options relative to that system for a particular user. For instance, a circuit gateway might check user IDs and passwords, or it might implement proxy connection authorization or other types of authentication services. A circuit firewall is also responsible for logging who came from where and went to what.
Circuit-switched Network A network design in which a dedicated physical circuit is established between the source and destination nodes before any data transmission can take place. Furthermore, this circuit must remain in place for the duration of a transmission.
CIX An acronym for commercial Internet exchange, a subscription organization consisting of a consortium of commercial and nonprofit regional network providers that began offering Internet service independent of the NSFNET backbone and without NSF’s restriction on traffic type. Today, CIX serves as an Internet interconnect site similar to a NAP.
Class I Repeater A type of repeater used in Fast Ethernet LANs. Class I repeaters support both of Fast Ethernet’s signaling schemes—100BASE-T4 and 100BASE TX/FX.
Class II Repeater A type of repeater used in Fast Ethernet LANs. Class II repeaters support only one of Fast Ethernet’s signaling scheme—100BASE-T4 or 100BASE TX/FX.
Class of Service (CoS) A data prioritization scheme that tags data with a specific priority level. Higher priority data get delivered before lower priority data.
CLEC An acronym for competitive local exchange carrier, which refers to a new telecommunication service provider formed after the Telecommunications Act of 1996 in the United States.
Client A networked device that requests resources from a server.
Client-Server. A model or paradigm that describes network services and the programs used by end users to access these services. The client side (or front end) provides a user with an interface for requesting services from the network, and the server side (or back end) is responsible for accepting user requests for services and providing these services transparent to the user.
Coaxial Cable A type of cable that consists of a single-wire conductor, surrounded by a dielectric material and two types of shielding, a foil shield and a braided shield, arranged concentrically and encased in a PVC or Teflon outer jacket.
Collapsed Backbone A term used to describe a network topology in which all LAN segments are interconnected via a bridge or switch, which serves as the network backbone.
Collision The term used to describe what happens when two or more nodes attempt to transmit data simultaneously on an Ethernet/802.3 network: Their signals collide resulting in a collision.
Collision Domain A "field" within a single Ethernet/802.3 network where two nodes can cause a collision. In the case of a single-segmented Ethernet/802.3 LAN, the independent segment represents the collision domain; in a multisegmented Ethernet/802.3 LAN, the collective segments comprise the collision domain.
Committed Burst (Bc) A term used in frame relay to denote the maximum amount of data a provider guarantees to deliver within a specified time period, T. CIR = Bc/T. Most providers use a one-second time interval to calculate the average amount of bandwidth utilization. Thus, CIR is usually equal to Bc. The difference between these two parameters is their units. CIR is measured in bps; Bc is measured in bits. See also excessive burst.
Committed Information Rate (CIR) The amount of throughput a frame relay provider guarantees to support under normal network loads. A CIR, which is assigned to a PVC when the network is initially configured, can range from 16 kbps to T3 (44.8 Mbps) and is the minimum guaranteed throughput of a PVC. If a PVC’s assigned CIR is greater than or equal to the average amount of traffic transmitted across a PVC over a specified period of time (e.g., one second), then data transmissions are guaranteed. If the assigned CIR is less than this average, then data transmissions are not guaranteed.
Compression A process that codes repetitive patterns within a data set. Compressed files can be sent at a faster rate than uncompressed files.
Computer Emergency Response Team (CERT) A formal organization operated by the Software Engineering Institute at Carnegie Mellon University and dedicated to addressing computer and network security issues. CERT also serves as a clearinghouse for identifying and resolving security "holes" in network-related software or operating systems.
Computer Network A collection of computers and other devices that use a common network protocol to share resources with each other over a network medium.
Conductor That part of a wire which serves as the medium for the physical signal. It is composed of either copper wire, glass, or plastic fiber. In the case of copper, the wire can be stranded (composed of several thin wires) or solid (a single, "thick" strand). Furthermore, the thickness of a wire is given in terms of gauge, which represents the conductor’s diameter. The lower the gauge, the thicker the wire. Most often, wire gauges are expressed in terms of AWG—American Wire Gauge—which is a classification system for copper wire based on a wire’s cross-section diameter.
Congestion A term used to describe a situation when a network is consumed with excessive network traffic (i.e., lots of packets) resulting in performance degradation. Congestion occurs when routers are too slow, causing queues to lengthen, or when routers are too fast, causing queues to build up whenever input traffic is greater than the capacity of output lines. The ultimate level of congestion is known as deadlock, which occurs when one router cannot proceed until a second router does something, and the second router cannot
proceed because it is waiting for the first router to do something. Congestion control is provided by layer 3 of the OSI model.
Connectionless Service A type of service in which messages are partitioned into packets and routed through the network. Each packet is independent of the other packets that carry parts of the message, and each packet carries a destination address. Unlike connection-oriented service, no physical link is established between sending and receiving nodes prior to data transmission.
Connection-oriented Service A type of service in which prior to the transfer of data a physical (and virtual) link is established between the sending and receiving nodes. This link remains in effect for the duration of the session. After the session is completed, the link is removed. Characteristics of a connection-oriented service include: wasted bandwidth (link must remain established even during idle periods of a transmission); a high potential for a hung network (there is always a possibility that a link will not be terminated); and guaranteed sequential arrival of packets at the destination node.
Connector A layer 1 device that attaches network components together.
Consortia Standards Network standards that are designed and agreed upon by a group of vendors who have formed a consortium for the express purpose of achieving a common goal. These vendors pledge their support for the standards being developed by the consortium and also develop and market products based on these mutually agreed upon set of standards.
Contention A phenomenon in which more than one node competes to access a shared medium simultaneously.
Contention Protocol A network protocol that specifies procedures nodes are to follow when competing for access to the same communications channel at the same time. Also called random access protocol.
CRC An acronym for cyclic redundancy check.
CRC Checksum The result of a polynomial division that uses a predetermined generator polynomial as the divisor.
CRC Error An invalid CRC checksum.
Crosstalk Electrical interference (i.e., noise) that occurs when energy radiated from one wire-pair of a twisted pair wire "spills over" into another pair. In one type of crosstalk, called near-end crosstalk (abbreviated NEXT), a signal on the transmit pair is so strong that it radiates to the receive pair. A direct consequence of this spilled-over radiation is that the receiving device cannot decipher the real signal.
Cryptology The practice or art of encoding messages.
CSMA An acronym for carrier sense multiple access, which serves as the basis for various random access protocols. CSMA-based protocols include one-persistent CSMA, nonpersistent CSMA, CSMA with collision Detection CSMA/CD), and CSMA with collision avoidance (CSMA/CD).
CSMA with Collision Avoidance (CSMA/CA) A variant of CSMA/CD except that it specifies a implementation scheme for collision avoidance instead of collision detection.
CSMA with Collision Detection (CSMA/CD) A variant of either 1-persistent or nonpersistent CSMA that specifies what a node is to do upon detecting a collision. One-persistent CSMA/CD is the MAC sublayer protocol used in Ethernet/802.3 LANs.
CSU An acronym for channel service unit, which is a device used for terminating Tx circuits. A CSU regenerates the signal, monitors the line for electrical anomalies, provides proper electrical termination, performs framing, and provides remote loopback testing for diagnosing line problems. Usually combined with a DSU to form a single unit called a CSU/DSU or DSU/CSU.
CSU/DSU An acronym for channel service unit/data (or digital) service unit, which is a device that combines the functions of a CSU and a DSU. A CSU/DSU works exclusively with digital signals; it provides an interface between a digital computing device and a digital transmission medium.
Cut-Through A term used to describe a network switch architecture. Cut-through switches begin forwarding frames from one switch port to another as soon as the frame’s destination address is read.
Cyclic Redundancy Check (CRC) An error detection method that constructs a polynomial whose terms’ coefficients are the values of each of the bits of a data frame. This polynomial is divided by a predetermined generator polynomial. The remainder of this division, called the CRC checksum, is then assigned to a frame’s checksum field. The most common CRC used in most LAN protocols is CRC-32, a 32-bit checksum.
D Channel A 16 kbps or 64 kbps ISDN circuit that is used to carry signal and control information for circuit-switched user data. The D channel transmits call initiation (call- setup) and termination (call tear-down) information between an ISDN device and the telco’s central office for each B channel. The D channel also can be used to transmit packet-switched user data (provided that no signal or control information is needed), data from security alarm signals of remote sensing devices that detect fire or intruders, and low speed information acquired from telemetry services such as meter reading. The "D" stands for "delta."
Datagram A grouping of bits organized as a logical unit of data at the network layer. IP datagrams serve as the Internet’s primary unit of information. In the OSI model, a datagram is generically referred to as a packet.
Data Link Layer The second layer (layer 2) of the OSI Reference Model. The data link layer regulates and formats transmission of information from software on a node to the network cabling facilities. This layer is partitioned into two sublayers: The logical link control sublayer (LLC), which provides framing, flow control, and error control; and the media access control sublayer (MAC), which media access management protocols for accessing a shared medium.
Data Rate A measure of the amount of data that can be transferred over a communications medium in a given period. Data rate is measured in bits per second (bps) and can vary considerably from one type of channel to another.
DB Connector Layer 1 device that serves as an interface between a computer and a peripheral device such as a printer or external modem; "DB" stands for "data bus.")
DCE An acronym for data communications equipment. Generally used as a synonymous term for modem. A DCE device is placed between DTEs and is responsible for establishing, maintaining, and terminating the link connecting the two DTEs.
DCE-to-DCE Rate The speed at which two modems "talk" to each other. This rate is fixed and is a function of a modem’s speed. Typical rates are 14,400 bps (V.32), 28,800 bps (V.34), and 57,600 bps (V.90).
Decentralized System Computer systems that are independent of each other, and maintain separate databases germane to specific activities.
Decryption The process of taking an encrypted (coded) message and translating it into its original, meaningful form.
De Facto Standards Network standards, placed in the public domain, that have been met with widespread industry acceptance instead of formal approval from a standards organizations ("De facto" is Latin for "from the fact.")
De Jure Standards Network standards approved by a formal, accredited standards organization such as ANSI or ITU. ("De jure" is Latin for "by right, according to law.")
Demand Access Multiplexing (DAM) A multiplexing technique in which a pool of frequencies is managed by a "traffic cop." Pairs of communications frequencies are assigned to a requesting station—one pair for transmission, a second pair for reception ("demand"). These two pairs of frequencies are connected to another set of frequencies ("access"). When one or both stations are finished communicating, the allocated frequencies are de- allocated and returned to the frequency pool, where they are made available for other incoming requests ("multiplexing").
Demand Priority A MAC sublayer protocol used in 100VG-AnyLAN networks. Demand priority specifies the manner in which repeater hubs poll their ports to identify which nodes have data to transmit and the order of these transmissions.
DES An acronym for data encryption standard, which is a specific coding technique developed by the National Institute of Standards and Technology (formerly the National Bureau of Standards) and IBM for protecting sensitive data during transmission.
Desktop Another name for a networked device. See workstation.
Device Any entity that is connected to a network. Examples include terminals, printers, computers, or special network-related hardware units such as communication servers, repeaters, bridges, switches, and routers. Local or sending devices originate communications; remote or receiving devices are the recipient of such communications.
Differential Manchester Encoding A data transmission encoding scheme similar to Manchester—each bit-period is partitioned into two intervals and a transition between "high" and "low" occurs during each bit-period. In differential Manchester coding, though, the interpretation of these low-to-high and high-to-low transitions is a function of the previous bit-period. The presence of a transition at the beginning of a bit period is coded 0, and the absence of a transition at the beginning of a bit period is coded 1. Differential Manchester encoding is used for clocking purposes only.
Diffused IR A "broadcast" infrared transmission method in which a transmitter "floods" a specific area with a strong infrared signal that is spread over a wide angle. The IR signal is transmitted by reflecting off of ceilings, walls, and other surfaces.
Digital Refers to any device or signal that varies discreetly in strength or quantity between two values, usually zero and one. Zero implies "off"; one implies "on." Digital signals are represented as binary digits called "bits," and are discrete.
Digital Certificate An electronic passport that consists of a numerical pattern, value, or key and used for personal identification. Creating a digital certificate involves a user identifying a specific personal trait to a trusted third party, which issues the certificate.
Digital Communication Refers to any type of communication in which data are represented in the form of binary digits.
Digital Signature A security authorization method in which a user "signs" a document so that the document’s authenticity can be confirmed by checking the signature. A digital signature proves a message was not modified.
Digital Subscriber Loop The formal term used to denote the local loop, which is the circuit between a customer’s premise equipment (CPE) and the telco’s equipment.
DIN Connector Similar to a DB connector, but is circular instead of rectangular and typically used to connect a keyboard to a computer; "DIN" stands for "Deutsche Industrie Norm," a German industrial standard.
Directed IR A "point-to-point" infrared transmission method that requires an unobstructed line-of-sight connection between transmitter and receiver. It is basically a "point and beam" medium.
Discard Eligibility The name of a field in a frame relay frame, which, if set to 1 by an end node, denotes that the frame can be discarded in the presence of congestion Discarded frames will then be retransmitted at a later time when congestion has subsided.
Distance-vector Algorithm A routing algorithm that determines the distance between source and destination nodes by calculating the number of router hops a packet traverses en route from the source network to the destination network. An example of a distance- vector algorithm is the Bellman-Ford algorithm.
Distributed System Computers that are linked together to provide, in a transparent manner, the required computing resources and information processing needs of an entire organization. Distributed systems bear the greatest resemblance to computer networks.
DLCI An acronym for data link connection identifier, which is a term used in frame relay to denote virtual circuit addresses assigned to PVCs or SVCs.
Domain Name A logical name assigned to an IP address and used as another type of addressing construct for identifying Internet nodes. The translation between logical name and IP address is called name resolution, which is provided by a domain name service.
Domain Name Service (DNS) An Internet translation service that resolves domain names to IP addresses and vice versa. DNS is provided by DNS servers.
DQDB An acronym for distributed queue dual bus, which is a data link layer protocol (IEEE 802.6) that specifies the medium access method for MANs. Used in SMDS.
DS-0 A single, digital voice channel rated at 64 kbps. The notation DS-0 stands for digital signal at level 0, which refers to a voice channel multiplexed into a digital signal.
DS-1 A digital signal that carries 24 DS-0 channels plus one 8 kbps channel reserved for framing for an aggregate bandwidth of 1.544 Mbps. A T1 circuit carries a DS-1 signal.
DS-2 A digital signal that carries 4 DS-1 channels for an aggregate bandwidth of 6.312 Mbps. A T2 circuit carries a DS-2 signal.
DS-3 A digital signal that carries 28 DS-1 channels for an aggregate bandwidth of 44.736 Mbps. A T3 circuit carries a DS-3 signal.
DS-4 A digital signal that carries 168 DS-1 channels for an aggregate bandwidth of 274.176 Mbps. A T4 circuit carries a DS-4 signal.
DSL An acronym for digital subscriber line, which is a technology that enables data, voice, and video to be mixed and carried over standard analog, (copper) telephone lines. This is accomplished by using the unused frequencies that are available on a telephone line. Thus, DSL can deliver data services without interfering with voice transmissions.
There are at least nine DSL variants: ADSL, ADSL lite, HDSL, HDSL 2,IDSL, RADSL, SDSL, UDSL, and VDSL.
DSLAM An acronym for DSL access multiplexer, which is a device that aggregates DSL signals so they can be transferred directly into a data switch for transmission across the telco’s data network backbone.
DSSS An acronym for direct sequence spread spectrum, which is a physical layer technology used in wireless LANs (IEEE 802.11). DSSS operates by spreading a signal over a wide range of the 2.4 GHz band.
DSU An acronym for data (or digital) service unit, which is a device used for terminating a Tx circuit. A DSU provides the interface (usually V.35, a type of serial interface) for connecting a remote bridge, router, or switch to a Tx circuit. The DSU also provides flow control between the network and the CSU. Usually combined with a CSU to form a single unit called a CSU/DSU or DSU/CSU.
DTE An acronym for data terminal equipment. Computers (PCs, workstations) are data terminal equipment. DTEs are the end points of a link and communicate through their serial ports or expansion buses. See also data communications equipment (DCE).
DTE-to-DCE Rate The speed at which a computer "talks" to its modem. Typical rates include a 4:1 compression ratio between DTE and DCE speeds. Thus, for a V.34 modem (28,800 bps), the DTE-DCE rate is 115,200 bps. This rate is user configurable.
Dual-attachment Station (DAS) An FDDI node that is connected to two full, dual-fiber rings and have the ability to reconfigure the network to form a valid network from components of the two rings in case of a failure. A DAS is also called Class A node.
E.164 An ITU-T standard network addressing format that resemble telephone numbers. E.164 addresses are 15 decimal digits long and include a country code, area or city code, and a local number. Country codes are two or three digits long and consist of a zone code followed by a one- or two-digit national identifier. Area or city codes are up to four digits long. If an address contains less than 15 digits, then it is padded with hexadecimal Fs. Australia does not use city codes, and the United States and Canada use the zone code 1 followed by a three-digit area code and a seven digit local number in lieu of county codes.
E-1 Describes the multiplexing of 30 separate 64 kbps voice channels, plus one 64 kbps control channel, into a single, wideband digital signal rated at 2.048 Mbps. E-1 is the basic telecommunications service used in Europe.
E-2 A multiplexed circuit that combines four E-1 circuits and has an aggregate bandwidth of 8.448 Mbps.
E-3 A multiplexed circuit that combines 16 E-1 circuits and has an aggregate bandwidth of 34.368 Mbps.
E-4 A multiplexed circuit that combines 64 E-1 circuits and has an aggregate bandwidth of 139.264 Mbps.
E-5 A multiplexed circuit that combines 256 E-1 circuits and has an aggregate bandwidth of 565.148 Mbps.
E-commerce Short for electronic commerce, which involves using the Internet for credit card purchases of items such as automobiles, airline tickets, computer hardware and software, and books.
EGP An acronym for exterior gateway protocol, which refers to any Internet interdomain routing protocol used to exchange routing information with other autonomous systems. Also refers to Exterior Gateway Protocol, which is a specific EGP defined in RFC 904. Another EGP is the Border Gateway Protocol (BGP), defined in RFC 1105 and RFC 1771. Both EGP and BGP are part of the TCP/IP protocol suite. Of the two, however, BGP has evolved into a robust Internet routing protocol and the term "Border Gateway Protocol" is used in favor of the term "Exterior Gateway Protocol."
EIGRP An acronym for enhanced IGRP, which is routing protocol designed by Cisco that combines the best features of distance-vector and link-state routing protocols.
Encapsulation A process in which a packet or frame is enclosed or "wrapped" in a specific protocol header. For example, routers typically perform protocol encapsulation in which packets from one network protocol are wrapped into the header of another network protocol so the packet can be transmitted to a different network. Also called tunneling.
Encryption The process of coding a message so that it is incomprehensible to unauthorized users. When retrieved by authorized users, encrypted messages are then reconverted (i.e., decoded) into meaningful text. Encrypted output is called ciphertext.
Error Control The process of guaranteeing reliable delivery of data. Error control can be provided through error detection or error correction.
Error Correction The process in which a destination node, upon detecting a data transmission error, has sufficient information to correct the error autonomously. Error correction implies error detection.
Error Detection The process in which a destination node detects a data transmission error and requests a retransmission from the sending node. Error detection is also called error correction through retransmission.
Ethernet A local area network protocol developed jointly by Xerox, Intel, and Digital Equipment Corporation (DEC) at the Xerox Palo Alto Research Center (PARC) in the mid-1970s. The name "Ethernet" was derived from the old electromagnetic theoretical substance called luminiferous ether, which was formerly believed to be the invisible universal element that bound together the entire universe and all its associated parts. Thus, an "ether" net is a network that connects all components attached to the "net."
Excessive Burst (Be) A term used in frame relay to denote the maximum amount of uncommitted data a provider will attempt to deliver within a specified time period. A provider will guarantee a committed burst of Bc bits and will attempt to deliver (but not guarantee) a maximum of Bc + Be bits.
Exchange Access SMDS (XA-SMDS) A special SMDS service through which LECs offered SMDS to IECs for delivery across LATAs.
Extranet A popular networking term that describes an interconnection from an internal intranet to a customer or noncompany network that is not the Internet connection.
4B/5B A data encoding method, which stands for four bits in five baud, or four-bit to five-bit, used in FDDI networks.
5-4-3 Repeater Rule A general rule of thumb to follow when configuring an Ethernet/ 802.3 LAN to ensure that it follows IEEE specifications. The 5-4-3 rule requires: no more than 5 segments of up to 500 m each; no more than 4 repeaters; and no more than 3 segments can have end nodes connected to them. This rule is also known as the 4-repeater
rule, or the 5-4-3-2-1 rule. In the latter, the "2" implies that two of the five segments are used as interrepeater links, and the "1" implies that a configuration using the maximum parameters permitted results into one collision domain.
Fast Ethernet 100 Mbps Ethernet (IEEE 802.3u). Three different media specifications are defined: 100BASE-TX, 100BASE-T4, and 100BASE-FX.
FDDI Fiber Distributed Data Interface. FDDI networks are described by ANSI standard X3T9.5 and created in 1986 for interconnecting computer systems and network devices typically via a fiber ring topology at 100 Mbps.
FECN An acronym for forward explicit congestion notification, which is a one-bit field in a frame relay frame that is set to 1 by a frame relay switch to denote that a frame transmitted toward the receiving node experienced congestion.
FDDI-II A now defunct second generation FDDI technology that was intended to handle traditional FDDI network traffic as well as synchronous, circuit-switched PCM data for voice or ISDN systems.
FHSS An acronym for frequency hopping spread spectrum, which is a physical layer technology used in wireless LANs (IEEE 802.11). FHSS operates by transmitting short bursts of data on different frequencies. One burst is transmitted on one frequency, a second burst is transmitted on a second and different frequency, and so forth.
Fiber-optic Cable A type of cable that carries data signals in the form of modulated light beams. The cable’s conductor can be either glass or plastic. Fiber-optic cable is immune to electromagnetic interference (EMI) and other types of externally induced noise, including lightning, it is unaffected by most physical factors such as vibration, its size is smaller and its weight lighter than copper, it has much lower attenuation per unit of length than copper, and it can support very high bandwidth. Two general types are available: single-mode fiber and multimode fiber.
Fibre Channel A family of ANSI standards that defines a specific communications interface for high-speed data transfers between different hardware systems. Applications include the medical profession, where large images (e.g., 100 MB+ X-rays) are transferred from a scanner to a computer to a screen, and the electronic publishing industry, where large files are transferred from an designer/creator’s machine to a publisher’s computer. It has also become the "backbone" of high-speed data storage systems.
Firewall A device or product that allows systems or network manager to restrict access to components on a network. Five generally accepted types of firewalls are used on Internet connections are frame-filtering, packet-filtering, circuit gateways, stateful and application gateways, and proxy servers.
FIX An acronym for federal Internet exchange, which is an Internet interconnect site similar to a NAP.
Flow Control A process that controls the rate at which data messages are exchanged between two nodes. Flow control provides a mechanism to ensure that a sending node does not overwhelm a receiving node during data transmission.
Fractional T1 T1 service that is sold in 64 kbps increments.
FRAD An acronym for frame relay access device, which is a term used to denote any frame relay end node.
Fragmenting A process in which a packet is broken into smaller units to accommodate the maximum transmission unit a physical network is capable of supporting. Fragmented packets are sent to the destination separately and then reassembled at the destination node before it is passed to the higher levels. In IP, reassembly of a datagram occurs at the destination node and not at any of the intermediary nodes the packet traverses.
Frame A specially formatted sequence of bits that incorporates both data and control information.
Frame-filtering Firewall A firewall device or product that filters (permits or denies access) at the data link layer by examining frames for both layout and content.
Framing A data link layer process that partitions a bit stream into discrete units or blocks of data called frames.
Frame Relay A public WAN packet-switching protocol that provides LAN-to-LAN connectivity. Its name implies what it does, namely, relays frames across a network between two sites. Frame relay was originally part of the ISDN standard.
Frequency Division Multiplexing (FDM) A multiplexing technique that partitions the available transmission frequency range into narrower bands (subfrequencies), each of which is a separate channel. FDM-based transmissions are parallel in nature.
Full-duplex Transmission A data transmission method that involves the simultaneous sending and receiving of data in both directions.
GAN An acronym for global area network, which refers to a collection of WANs that span the globe.
Gateway A software application that converts between different application protocols. The host on which this software resides is called a gateway machine. Historically, this term also refers to a router in the IP community.
Gigabit Ethernet 1000 Mbps Ethernet (IEEE 802.3z).
Geostationary Earth Orbit (GEO) Satellite A satellite placed into orbit at an altitude of 22,000 miles (36,000 kilometers) above the equator. GEO satellites traverse their orbits at approximately the same rate as the Earth rotates. Thus, the satellite appears stationary with respect to the Earth’s rotation. Also call Geosynchronous Earth Orbit. Only eight GEO satellites are needed to provide global communications coverage.
GOSIP An acronym for Government OSI Profile, which mandated all government organizations purchase OSI-compliant networking products beginning in 1992. In 1995, however, GOSIP was modified to include TCP/IP as an acceptable protocol suite for GOSIP compliance.
Graded-index Multimode Fiber A type of multimode fiber in which variations in the density of the core medium change its index of refraction such that light is refracted (i.e., bends) toward the center of the fiber.
H Channel An ISDN channel used for transmitting user data (not signal or control information) at higher transmission rates than a B channel provides. Four H channels are defined: H0 (six B channels; 384 kbps); H10 (United States-specific; aggregates 23 B channels; 1.472 Mbps); H11(equivalent of North American DS-1; 24 B channels; 1.536 Mbps); and H12 (European-specific; comprises 30 B channels; 1.920 Mbps).
Half-duplex Transmission A data transmission method in which may travel in either direction—from sender to receiver or receiver to sender—but only one unit can send at any one time. While one node is in send mode, the other is in receive mode.
Harmonic Motion The basic model for vibratory or oscillatory motion. Examples include mechanical oscillators such as mass-spring systems and pendulums; periodic motion found in the earth sciences such as water waves, tides, and climatic cycles; and electromagnetic waves such as alternating electric currents, sound waves, light waves, radio waves, and television waves.
HDSL An acronym for high bit-rate digital subscriber line, which is a DSL variant that provides symmetrical service at T1 rates over 2 pairs of UTP, and E1 rates over 3 pairs of UTP. Telephone service not supported. Applications include connecting PBXs, serving as an alternative to T1/E1; suitable for campus networks and ISPs.
HDSL 2 A modified HDSL designed and packaged for corporate clients.
Hertz A measure of frequency in cycles per second. A frequency rate of one cycle per second is defined as one hertz (abbreviated Hz). Named in honor of Heinrich Rudolf Hertz (1857-1894), a German physicist who in the late 1880s was the first to produce radio waves artificially.
HFC An acronym for hybrid fiber cable, which describes a cable TV cable plant that has fiber-optic cable between the head end and neighborhood distribution sites, but coaxial cable between the neighborhood distribution and residential homes and businesses.
Hold-down A strategy used by RIP that requires routers to not update their routing tables with any new information they receive for a prescribed period of time, called the hold-down time. Designed to prevent routing loops. Hold-down is not standardized.
Hop A term used to describe the passage of a packet through an intermediate gateway (router) en route to another network. For example, if a packet transverses through two routers in reaching its final destination, then we say the destination is two hops away.
Host A networked computer system (see workstation). Also used to describe a computer system that provides service to users (see server).
Hub Generically, any device that connects two or more network segments or supports several different media. Examples include repeaters, switches, and concentrators.
Hybrid Switching A data transmission method that combines the principles of circuit and packet-switching. This technique first partitions a message into packets (packet- switching) and transmits each packet via a dedicated circuit (circuit-switching). As soon as a packet is ready for transmission, a circuit meeting appropriate bandwidth requirements is established between the sending and receiving nodes. When the packet reaches its destination, the circuit is broken down so that it can be used again.
IBM Cable System (ICS) A copper wire classification system established by IBM that specifies nine cable "types" (1 through 9). Of the nine "types" defined, specifications are available for only seven; types 4 and 7 are not defined.
ICMP An acronym for Internet control message protocol, which uses an IP datagram to carry messages about the communications environment of the Internet.
IDSL An acronym for ISDN-like digital subscriber line, which is a DSL variant that provides symmetrical service at a maximum of 144 kbps each way. Uses ISDN hardware.
IEC See IXC.
IEEE An acronym for Institute of Electrical and Electronics Engineers, which is a professional society of engineers, scientists, and students. One of its many activities is to act as a coordinating body for computing and communication standards.
IEEE 802 The primary IEEE standard for the 802.x series for LANs and MANs.
IEEE 802.1 IEEE standard that defines an architectural overview of LANs.
IEEE 802.2 IEEE standard that defines the Logical Link Control, which describes services for the transmission of data between two nodes.
IEEE 802.3 IEEE standard that defines the Carrier Sense Multiple Access/Collision Detection (CSMA/CD) access method commonly referred to as Ethernet. Supplements include 802.3c (10 Mbps Ethernet); 802.3u (100 Mbps Ethernet known as Fast Ethernet), and 802.3z and 802.3ab (1000 Mbps Ethernet known as Gigabit Ethernet).
IEEE 802.4 IEEE standard that defines the token bus network access method.
IEEE 802.5 IEEE standard that defines the logical ring LAN that uses a token-passing access method; known also as Token Ring.
IEEE 802.6 IEEE standard that defines metropolitan area networks (MANs).
IEEE 802.7 IEEE standard that defines broadband LANs (capable of delivering video, data, and voice traffic).
IEEE 802.9 IEEE standard that defines integrated digital and video networking—Integrated Services LANs (ISLANs).
IEEE 802.10 IEEE standard that defines standards for interoperable LAN/MAN security services.
IEEE 802.11 IEEE standard that defines standards for wireless media access control and physical layer specifications.
IEEE 802.12 IEEE standard that defines the "demand priority" access method for 100Mbps LANs; known also as 100 Base-VG or 100VG-AnyLAN.
IEEE 802.13 (Defines nothing—IEEE was concerned about the superstitious overtones associated with "13.")
IEEE 802.14 IEEE standard that defines a standard for Cable-TV based broadband communication.
IGP An acronym for interior gateway protocol, which is any intradomain Internet protocol used to exchange routing information within an autonomous system. Examples include RIP, RIP-2, OSPF, IGRP, and Enhanced IGRP (EIGRP).
IGRP An acronym for interior gateway routing protocol, which was developed by Cisco to address some of the problems associated with routing in large, heterogeneous networks.
ILEC An acronym for incumbent local exchange carrier, which is the contemporary name given to the RBOCs relative to the United States Telecommunications Act of 1996.
Impedance A measure of the opposition to the flow of electric current in an alternating current circuit. Measured in ohms (abbreviated by the Greek symbol, omega, ¾), impedance is a function of capacitance, resistance, and inductance. Impedance mismatches, caused by mixing cables of different types with different characteristic impedances, can result in signal distortion.
Impulse Noise Electrical noise that consists of intermittent, undesirable signals induced by external sources such as lightning, switching equipment, and heavy electrically operated machinery such as elevator motors and copying machines. Impulse noise increases or decreases a circuit’s signal level, which causes the receiving equipment to misinterpret the signal.
Infrared (IR) A line-of-sight transmission method that uses electromagnetic radiation of wavelengths between radio waves and visible light, operating between 100 GHz and 100 THz (Terahertz). IR transmission can occur in one of two ways: directed and diffused.
Insulation Material surrounding the conductor of a wire. The insulation serves as a protective "barrier" to the conductor by preventing the signal from "escaping" and preventing electrical interference from "entering."
Intermodulation Noise Electrical noise that occurs when two frequencies interact to produce a phantom signal at a different frequency. Occurs in frequency-division multiplexed channels.
Internet When used as a noun and spelled with a lowercase i, "internet" is an abbreviation for internetwork, which refers to a collection of interconnected networks that functions as a single network. When used as a proper noun and spelled with a capital I, "Internet" refers to the world’s largest internetwork, which consists of hundreds of thousands of interconnected networks worldwide and based on a specific set of network standards (TCP/IP).
Internet Architecture Board (IAB) An organization that is part of the Internet Society responsible for the overall planning and designing of the Internet. Responsibilities include setting Internet standards, managing the publication of RFC documents, and resolving technical issues. Assigned to the IAB are the Internet Engineering Task Force and the Internet Research Task Force. Formerly known as the Internet Activities Board.
Internet Assigned Numbers Authority (IANA) An organization that has authority over all number spaces used in the Internet including IP addresses. IANA control will soon be transferred to the Internet Corporation for Assigned Names and Numbers (ICANN).
Internet Corporation for Assigned Names and Numbers (ICANN) A private, non- profit corporation with international representation expressly formed to assume the responsibilities currently being performed by IANA and other government organizations that provide domain name service.
Internet Engineering Task Force (IETF) An organization that is part of the Internet Architecture Board and primarily concerned with addressing short- or medium-term Internet engineering issues. Relies on the Internet Engineering Steering Group (IESG) to prioritize and coordinate activities.
Internet Registry (IR) A formal hierarchical system used for assigning IP addresses. From top to bottom, this hierarchy consists of IANA, Regional Internet Registries (RIR), and Local Internet Registries (LIR), and works as follows: IANA allocates blocks of IP address space to RIRs; RIRs allocate blocks of IP address space to their LIRs; LIRs then assign addresses to either end users or ISPs.
Internet Research Task Force (IRTF) An organization that is part of the Internet Architecture Board and primarily concerned with addressing long-term research projects. Relies on the Internet Research Steering Group (IRSG) to prioritize and coordinate activities.
Internet Society (ISOC) An international organization comprised of volunteers who promote the Internet as a medium for global communication and collaboration. ISOC is considered the ultimate authoritative organization of the Internet.
Internet2 A collaborative project of the University Corporation for Advanced Internet Development (UCAID), which comprises over 100 U.S. universities, government organizations, and private sector firms. Internet2’s mission is to develop advanced Internet tech
nologies and applications that support the research endeavors of colleges and universities. Internet2 members use the vBNS to test and advance their research.
Interoperability The degree in which products (software and hardware) developed by different vendors are able to communicate successfully (i.e., interoperate) with each other over a network.
Intranet An internal network implementation of traditional Internet applications within a company or an institution.
Inverse Multiplexing The reverse of multiplexing. Instead of partitioning a single communication medium into several channels, an inverse multiplexer combines several "smaller" channels (i.e., low-speed circuits) into a single high-speed circuit. This technique is also sometimes generically called line aggregation.
IP An acronym for Internet protocol, a layer 3 connectionless protocol. IP receives data bits from the lower layer, assembles these bits into packets, called IP datagrams, and selects the "best" route based on some metric to route the packets between nodes. IP is the "IP" of TCP/IP.
IP Address A network address assigned to a node’s network interface and used to uniquely identify (locate) the node within the Internet. Two versions are currently implemented: IPv4 and IPv6.
IPSec An acronym for IP security, which is a suite of network security protocols that operates at layer 3 and provides address authentication, data encryption, and automated key exchanges between sender and receiver nodes.
IPv4 An acronym for Internet protocol version 4.
IPv4 Address An IP address based on IPv4. These addresses consist of 32 bits (0 through 31) partitioned into four groups of eight bits each (called octets), and organized into five classes (A through E) based on the values of bits 0 through 3.
IPv6 An acronym for Internet protocol version 6, which is an evolutionary replacement to IPv4. IPv6 maintains most IPv4 functions, relegates certain functions that either were not working or were rarely used in IPv4 as optional, and adds new functionality that is missing from IPv4. Sometimes called IPng (for next generation).
IPv6 Address An IP address based on IPv6. An IPv6 address consists of 128 bits and is 4 billion ? 4 billion times the size of the IPv4 address space (296 vs. 232). Unlike IPv4 addresses, IPv6 addresses use a colon as their delimiter (instead of a "dot" notation), and they are written as eight 16-bit integers expressed in hexadecimal form.
ISDN An acronym for integrated services digital network, which is a carrier service that is offered by telephone companies (telcos) and designed to transmit voice and non-voice (e.g., computer data, fax, video) communications on the same network. Also known as, I Still Don’t Need it, Innovative Services users Don’t Need, I Still Don’t kNow, and It’s Still Doing Nothing, response to ISDN’s long period of dormancy.
IS-IS An acronym for intermediate system to intermediate system, which is an intradomain routing protocol designed by OSI to run within an AS (called a "routing domain" in the OSI world). IS-IS uses a link-state routing algorithm to calculate least-cost paths, and is similar in operation OSPF. The formal title of this protocol is "Intermediate System to Intermediate System Intra-Domain Routing Exchange Protocol."
ISO An acronym for International Organization for Standardization, which develops and promotes networking standards worldwide.
Isochronous A term used to describe the delivery of time sensitive data such as voice or video transmissions. Networks that are capable of delivering isochronous service (e.g., ATM) preallocate a specific amount of bandwidth over a regular intervals to ensure that the transmission is not interrupted.
IsoEthernet Short for Isochronous Ethernet, which is an IEEE standard—IEEE 802.9a, designed to support time-sensitive applications such as videoconferencing and telephony. IsoEthernet runs both conventional 10 Mbps Ethernet and ISDN B channels over the same network. The Ethernet channel is used for normal data networking needs; the ISDN B channels are used for time-sensitive applications.
ISP An acronym for Internet Service Provider, which is an organization that provides its customers with access to the Internet.
ITU An acronym for International Telecommunications Union, which is a global standards organization. ITU is the former CCITT.
IXC An acronym for inter-exchange carrier, (alternatively, IEC), which is any company that provides long distance telephone and telecommunications services. Examples include AT&T, Sprint, British Telecom (BT), and MCI Worldcom.
Jabber An oversized Ethernet/802.3 frame and an invalid CRC checksum.
Kerberos A client-server network security authentication system, developed at MIT, and based on DES encryption. It is an Internet standard that uses a three-pronged approach for authentication: a database that contains users’ rights, an authentication server, and a ticket- granting server. Kerberos is named after Cerberus, the three-headed dog in Greek mythology that guarded the gates to Hades.
LAN An acronym for local area network, which is a network that generally interconnects computing resources within a moderately sized geographical area. This can include a room, several rooms within a building, or several buildings of a campus. A LAN’s range is usually is no more than 10 km in radius).
LANE An acronym for LAN emulation, which is an ATM protocol that specifies a technology that enables ATM to emulate Ethernet/802.3 or token ring networks. In ATM’s protocol hierarchy, LANE is above AAL5 in the ATM adaptation layer. The LANE protocol defines a service interface for the network layer that functions identical to the one used by Ethernet/802.3 and token ring LANs. Data that cross this interface are encapsulated in the appropriate MAC sublayer format.
LAP-D An acronym for link access protocol–D channel, which is an ITU-T standard on which the ISDN D channel is based.
LAPM An acronym for link access procedure for modems, which uses CRC and ARQ for error control. CRC is used for error detection; ARQ prevents the modem from accepting any more data until the defective frame has been retransmitted successfully. V.42’s default is LAPM. Thus, if a connection is being initialized between two V.42 compliant modems, they will use LAPM for error control. If one of the modems is not V.42 compliant, then the modems will negotiate to use MNP 1–4.
LATA An acronym for local access and transport area, which is a specific geographical region in which a local exchange carrier (LEC) provides local telephone and telecommunications services in the United States. There are 195 LATAs. Services that cross LATA boundaries are provided by inter-exchange carriers (IECs).
Latency The amount of delay a network device introduces when data frames pass through it. It is the amount of time a frame spends "inside" a network device. For example, switch latency is usually measured from the instant the first bit of a frame enters the device to the time this bit leaves the outbound (i.e., destination) port.
Layer 3 Switch A layer 2 switch that is capable of examining layer 3 header information, which is then used to filter network protocols or broadcasts. Also refers to a router that is capable of performing router table lookups and packet forwarding at hardware speeds via application specific integrated circuit (ASIC) chips.
Layer 4 Switch A router that is capable of examining upper layer (layers 4 through 7) information to make routing decisions. It is more appropriate to refer to layer 4 switches as either layer 2 or layer 3 application switches because application information from upper layers is being used for routing decisions.
Lightwave Wireless A line-of-sight laser-based connection facility that allows long-distance light-based wireless networking without the need to install cable.
Line-of-Sight A type of wireless transmission that requires the transmitter and receiver be able to "see" each other, that is, they must be in each other’s "line-of-sight."
Line Set A term used by the National ISDN Users’ Forum to describe the number of multiplexed B and D channels, and the type of ISDN service supported.
Link-state Algorithm A routing algorithm in which routers send each other information about the links they have established to other routers via a link state advertisement (LSA), which contains the names and various cost-metrics of a router’s neighbors. LSAs are flooded throughout an entire router’s domain. Thus, rather than storing actual paths (which is the case with distance-vector algorithms), link-state algorithms store the information needed to generate such paths. An example of a link-state algorithm is Dijkstra’s shortest path algorithm, which iterates on length of path to determine a shortest route.
Lobe The name of a token ring node, as defined in the IBM world.
Lobe Length A term used to identify the cable length between token ring nodes.
Local Loop Refers to the circuit that connects the telephone central office or exchange (sometimes called point of presence) with a customer’s location. In frame relay, this circuit is called the port connection or access line. Formally called digital subscriber loop.
Logical Link Control (LLC) Sublayer The top sublayer of the data link layer that provides framing, flow control, and error control Defined in IEEE 802.2.
Loop A network configuration in which nodes are connected via dedicated wiring instead of through a centralized hub (as is the case of a star design). Loops can be either simple (only one connection between any two nodes), partial (some nodes are interconnected by more than one link), and complete (every node has a connection to every other node). A loop is also referred to as a meshed design.
Low-Earth Orbit (LEO) Satellite A satellite placed in orbit at an altitude of 300 miles to 1,200 miles above the Earth. Depending on their orbit, a constellation of up to 48 LEO satellites are needed for global coverage.
L2F An acronym for layer 2 forward protocol, which provides tunneling between an ISP’s dial-up server and the network.
L2TP An acronym for layer 2 tunneling protocol, which defines a method for tunneling PPP sessions across a network. It combines PPTP and L2F.
Manchester Encoding A data transmission encoding scheme that differs from standard digital transmission schemes. Instead of "high" equaling "1" and "low" equaling "0," a timing interval is used to measure high-to-low transitions. Furthermore, instead of a timed transmission period being "all high" or "all low" for either 1 or 0, a 1 is sent as a half-time- period low followed by a half-time-period high, and a 0 is sent as a half-time-period high followed by a half-time-period low. Consequently, the end of the last bit transmitted is easily determined immediately following the transmission of the last bit.
MAE An acronym for metropolitan-area exchange, which is an Internet interconnect site similar to a NAP. The difference between the two is a NAP is funded by the National Science Foundation and MAE is not. There are currently two MAE points, one each on the east and west coasts of the United States and known as MAE East and MAE West.
MAN An acronym for metropolitan area network, which interconnects computing resources that span a metropolitan area such as buildings located throughout a local county or city. MANs generally refer to networks that span a larger geographical area than LANs but a smaller geographical area than WANs.
MAU Another term for a transceiver; "MAU" stands for "Media Attachment Unit." Also, Multistation Access Unit, which is a token ring hub.
Media Access Control (MAC) Sublayer The bottom half of the data link layer that provides media access management protocols for accessing a shared medium. Example MAC sublayer protocols include IEEE 802.3 (Ethernet) and IEEE 802.5 (token ring).
Medium The physical environment used to connect networked devices.
Medium-Earth Orbit (MEO) Satellite A satellite placed in orbit at an altitude of 6,000 miles to 12,000 miles above the Earth. A constellation of 20 MEO satellites are needed for global coverage.
Media The plural of medium.
Media Converter A layer 1 device that enables different network media to be connected to one another.
Meshed Design A term used to describe interconnectivity among multiple nodes or sites. In a fully-meshed design, every node or site is connected with every other node or site. In a partially-meshed design, only some nodes or sites are interconnected.
Metric A generic term used in routing to represent different quantities such as distance, number of router hops, and bandwidth.
Metro-Area Satellites A proposed satellite that consists of a specially equipped jets that fly 50,000 feet above cities.
Micron One micrometer (one millionth of a meter) and abbreviated by the symbol µm. Used in specifying the size of fiber-optic cable.
Microwave An RF transmission method that uses high frequency waves and operates at a higher frequency in the electromagnetic spectrum (usually above 900 MHz). Microwave transmissions are considered a line-of-sight medium.
MNP An acronym for Microcom Networking Protocol, which defines various levels of error correction and compression for modems.
MNP 1-4 The first four MNP levels used for hardware error control. All four levels are incorporated into V.42.
MNP 5 The fifth level of MNP that incorporates the MNP 1-4. Also uses a data compression algorithm that compresses data by a factor of 2 to 1.
MNP 6 The sixth level of MNP that supports V.22 bis and V.29.
MNP 7 The seventh level of MNP that improves MNP 5’s data compression algorithm to a 3 to 1 compression factor.
MNP 8 The eighth level of MNP that extends MNP 7; enables half-duplex devices to operate in full-duplex mode.
MNP 9 The ninth level of MNP that is used in a variety of circuits.
MNP 10 The tenth level of MNP that is used in cellular modems and in those situations where line quality is poor.
Modem An acronym modulator/demodulator. A modem transforms (modulates) a computer’s digital signal into analog form at the sending side so the signal can be carried across a standard telephone line. On the receiving side, a modem demodulates the signal— it reconverts the transmitted analog signal from the phone line to digital form before it is passed to the computer.
Multicast A data transmission that is destined to a group of recipients.
Multidrop Design A network configuration in which each system node is connected to a common cable plant and assigned a specific number that is used to communicate with the system and also to establish priority of when a system will be communicated with from a master control system. Primarily used in factories.
Multilink PPP (MP) An IP protocol that combines multiple physical links (i.e., telephone lines) into a single, high capacity channel. Unlike BONDING, which is implemented in hardware, MP is achieved via software. MP is also applicable to analog dialup connections.
Multimode Fiber A type of fiber-optic cable with a core diameter ranging from 50 µm to 100 µm. In multimode fiber, different rays of light bounce along the fiber at different angles as they travel through the core. This results in some degree of signal distortion at the receiving end. Multimode fiber can be of two types: graded-index or step-index.
Multiplexer A device that does multiplexing. Also called a mux for short.
Multiplexing A technique used to place multiple signals on a single communications channel. Multiplexing partitions a channel into many separate channels, each capable of transmitting its own independent signal, thereby enabling many different transmissions over a single medium.
NADH See North American Digital Hierarchy.
NAP An acronym for network access point, which is an Internet traffic exchange point that provides centralized Internet access to Internet service providers. A NAP serves as a critical, regional "switching station" where all different network backbone providers meet and exchange traffic on each other’s backbone.
NSAP An acronym for network service access point, which is an OSI addressing mechanism used by private ATM networks. NSAPs are 20-byte addresses and include a 13-byte prefix that can be used to identify a specific location including a country, region, or end system.
National Information Infrastructure (NII) A Federal policy initiative to facilitate and accelerate the development and utilization of the nation’s information infrastructure. The
perception of the NII is one of a "seamless web" of telecommunications networks consisting of computers, specialized databases, radios, telephones, televisions, and satellites. The NII is expected to provide consumers with convenient and instantaneous access to nearly any kind of information ranging from research results, to medical and educational material, to entertainment.
netstat A unix program that generates a local host’s routing table. Similar output can be generated on a Windows NT system using the command route print.
Network Architecture A formal, logical structure that defines how network devices and software interact and function; defines communication protocols, message formats, and standards required for interoperability.
Network Computer (NC) An inexpensive ($500 or less) network access device with functionality that allows some applications to be run, but not as complete as what would typically be found on a PC or a workstation of some sort. NCs are stripped-down systems that use the network to access their applications dynamically.
Network Diameter The overall length between a network’s two most remote nodes.
Network Ethics Refers to specific standards of moral conduct by network users for the responsible use of network devices and resources.
Network Interface Card A layer 2 device that performs standard data link layer functions, including organizing data into frames, transferring frames between the ends of a communication channel, and managing the link by providing error control, initialization, control termination, and flow control. A NIC" is also known as a LAN adapter, network adapter, network card, and network board. When used in Ethernet/802.e networks, a NIC is called an Ethernet card or adapter.
Network Operating System (NOS) Software that is installed on a system to make it network-capable. Examples include IBM’s LAN Server, Banyan’s VINES, and Novell’s NetWare (also known as IntranetWare). A NOS is independent of a computer’s native operating system—it is loaded "on top" of the computer’s operating system and provides the computer with networking capability based on a particular protocol. If an operating system provides built-in network support (e.g., Microsoft’s Windows NT and Sun’s Solaris), then the OS is called a networkable operating system.
Network Protocol Suite A set of related and interoperating network protocols. For example, the TCP/IP protocol suite consists of protocols for e-mail, web service, file transfers, and routing.
Network Security Refers to the proper safeguarding of everything associated with a network, including data, media, and equipment. It involves administrative functions, such as threat assessment, and technical tools and facilities such as cryptographic products, and network access control products such as firewalls. It also involves making certain that network resources are used in accordance with a prescribed policy and only by people who are authorized to use these resources.
Network Standards A formal set of rules, developed by and agreed upon by various organizations, defining hardware interfaces, communication protocols, and network architectures. Several standards exist, including de jure, de facto, proprietary, and consortia.
Network Termination Unit (NTU) A device that terminates E-1 circuits. An NTU provides broadly similar CSU/DSU functionality.
Network Topology The basic design of a computer network that details how key network components such as nodes and links are interconnected.
Next Generation Internet (NGI) An initiative to forge collaborative partnerships between the private and public sectors. Presumably, the vBNS will serve as the medium for NGI. Funding ($100 million for three years) has not been approved as of this writing.
Node Another name for a device. Usually used to identify computers that are network hosts, workstations, or servers.
Noise Any undesirable, extraneous signal in a transmission medium. There are generally two forms of noise—ambient and impulse. Noise degrades the quality and performance of a communications channel and is one of the most common causes of transmission errors in computer networks.
North American Digital Hierarchy (NADH) Describes a multiplexed T1 structure used in North America that combines multiple T1 lines into higher rated Tx circuits. For example, a T2 circuit consists of four multiplexed T1 circuits and has an aggregate bandwidth of 6.312 Mbps; a T3 link consists of 28 multiplexed T1 circuits with an aggregate bandwidth of 44.736 Mbps; and a T4 channel consists of 168 multiplexed T1 circuits and is rated at 274.176 Mbps.
nslookup A Unix and Microsoft NT program used to acquire the IP address of a domain name. This program can also be used for IP address resolution, which translates a numerical IP address to its corresponding domain name.
1-persistent CSMA A CSMA-based protocol in which a node continually waits a random period of time whenever it detects a busy channel. Once it senses an idle channel, it may then transmit data.
1-persistent CSMA A CSMA-based protocol in which a node continuously monitors a shared channel until it is idle and then seizes the channel and begins transmitting data. The "one" in 1-persistent represents the probability that a single waiting node will be able to transmit data once it detects an idle channel (p = 1).
OC An acronym for optical carrier, which is a fiber-optic digital transmission hierarchy used for SONET. OC rates range from OC-1, which is the equivalent of 28 DS-1 channels (51.84 Mbps) to OC-192, which is the equivalent of 5,376 DS-1 channels (9.953 Gbps). OC rates are the optical equivalent of STS rates.
OSI An acronym for open systems interconnection.
OSI Reference Model A network architecture for developing network protocol standards. The OSI Model formally defines and codifies the concept of layered network architecture. It uses well-defined operationally descriptive layers that describe what happens at each stage in the processing of data for transmission. The OSI Model consists of the following seven layers, which are numbered in descending order: Application (7), Presentation (6), Session (5), Transport (4), Network (3), Data Link (2), and Physical (1).
OSPF An acronym for open shortest path first, which is an interior gateway protocol based on a link-state algorithm. Designed for large, heterogeneous IP networks.
Oversized Frame An Ethernet/802.3 frame with more than 1,518 bytes but a valid CRC checksum.
Oversubscription A term used in frame relay to denote when the capacity of a frame relay connection into the frame relay network is less than the total bandwidth guaranteed by the provider. More specifically, the port speed is less than the aggregate CIR.
Packet The smallest unit of information that is transferred across a packet-switched network. In TCP/IP a packet is called a datagram.
Packet-filter Firewall A router or a dedicated device that filters network access at the network layer by examining packet addresses (source and destination), or specific network transport protocol type.
Packet-switched Network A network design that enables nodes to share a communications channel via a virtual circuit. Messages are partitioned into smaller messages called packets, which may contain only a few hundred bytes of data, accompanied by addressing information. Packets are sent to the destination node one at a time, at any time, and not necessarily in a specific order. The network hardware delivers the packets through the virtual circuit to the specified destination node, which is responsible for reassembling them in the correct order.
PAN An acronym for personal area network, which refers to residential computer networks being established in private homes. Sometimes called TANs for tiny area networks.
Parallel Communication A data transmission method in which the bits representing a character of data are transmitted simultaneously on separate channels. (Also called parallel transmission.)
Parity Refers to the use of an extra bit (called a parity bit or a redundant bit) to detect single-bit errors in data transmissions. Parity can be specified as even, odd, or none. Even parity means that there must be an even number of 1-bits in each bit string; odd parity means that there must be an odd number of 1-bits in each bit string; and no parity means that parity is ignored. The extra bit (i.e., the parity bit) is forced to either 0 or 1 to make the total number of bits either even or odd.
Partitioning A network configuration strategy that involves dividing a LAN into several separate (but still interconnected) network segments. Also called segmentation.
PBX An acronym for private branch exchange, a telephone exchange used within an organization to provide internal telephone extensions and access to the public telephone network; it is the modern day equivalent of what used to be called a switchboard.
PC Card A layer 2 plug-in adapter used in portable or laptop computers. Three different "types" are available. Type 1 cards are 3.3 millimeters thick and enhance the memory capabilities of a device; Type II cards are 5 mm thick and used for modems and network adapters for both Ethernet and token ring; Type III cards are 10.5 mm thick and generally either miniature hard disks or wireless NICs; and Type IV cards, when produced, will be approximately 16 mm thick and support hard disk drives that have a capacity greater than what is currently available from Type III cards. PC cards were formerly known as PCMCIA Cards.
PCMCIA Card A layer 2 device that was originally designed to serve as memory cards for microcomputers. These cards are now known as PC Cards. "PCMCIA" stands for Personal Computer Memory Card International Association.
Peer-to-Peer A model or paradigm on which some network communications and applications are based. In a peer-to-peer environment, each networked host runs both the client and server parts of an application.
Period The reciprocal of the frequency. It is the amount of time it take to complete a single cycle, that is, seconds per cycle.
PGP An acronym for pretty good privacy, which is a public key application developed by Phil Zimmerman for e-mail security.
Physical Layer The lowest layer (layer 1) of the OSI Reference Model. The physical layer translates frames received from the data link layer (layer 2) into electrical, optical, or electromagnetic signals representing 0 and 1 values, or bits. Abbreviated PHY in the documentation.
ping A unix and Microsoft NT program used to test the communication path between source and destination nodes. Ping is an ICMP-based application and is an acronym for packet Internet groper.
Pinout The electrical signals associated with each pin and connector. Also called pin assignment.
Plaintext An uncoded message; a message in its original, meaningful (uncoded) form.
Plastic Fiber A type of fiber-optic cable in which the fibers (i.e., conductors) are constructed of plastic instead of glass.
Plenum Cable Any type of cable that contains an outer sheath or "jacket" that is composed of a Teflon coating. Plenum cable is used for cable "runs" through a return air system. The Teflon coating provides a low-flame spread and does not release toxic fumes as quickly as PVC does in the case the cable burns during a fire. Both PVC and Teflon give off nasty toxic gases when burning. Teflon, however, is fire retardant and takes much longer to get to a burning point.
Point-to-Point Network A network design in which only adjacent nodes (nodes that are next to each other and only one hop away) can communicate with one another.
POP An acronym for point of presence, which usually refers to a telco’s central office or switching station.
Port Connection A term used in frame relay to denote the local loop. Also called access line.
Port Speed A term commonly used in frame relay to denote the data transmission rate in bits per second of the local loop.
POTS An acronym for plain old telephone system.
PPTP An acronym for point-to-point tunneling protocol, which provides encryption and authentication for remote dial-up and LAN-to-LAN connections. PPTP establishes two types of connections: A control session for establishing and maintaining a secure tunnel from sender to receiver, and a data session for the actual data transmission.
PRI An acronym for primary rate interface, which is an ISDN primary access channel that comprises either 23 (United States) or 30 (Europe) 64 Mbps B channels and one 64 kbps D channel. Commonly written as 23B + D, or 30B + D.
Private Link A term used to describe a communications channel that provides a private, dedicated link between two sites. Also commonly referred to as standard leased line.
Private Switch A term used to describe one application of an Ethernet switch. A private switch supports only one MAC address per port, which provides each node with its own dedicated 10 Mbps segment. This eliminates contention for the cable, thereby liberating the end nodes from performing collision detection.
Promiscuous Mode A state in which an Ethernet interface can be placed so that it can capture every frame that is transmitted on the network. For example, an Ethernet NIC set
in promiscuous mode collects all messages placed on the medium regardless of their destination address.
Propagation Delay The amount of time a signal takes getting from one point in a circuit to another.
Proprietary Standards Network standards that are developed in a manufacturer-specific manner. Their specifications are not in the public domain and are only used and accepted by a specific vendor.
Protocol An accepted or established set of procedures, rules, or formal specifications governing specific behavior or language. When applied to networks, a network protocol is a formal specification that defines the vocabulary and rules of data communication.
Proxy Server A device or product that provides network protection at the application level by using custom programs for each protected application. These custom-written application programs act as both a client and server and effectively serve as proxies to the actual applications. Also called application gateway firewall are or proxy gateway.
PSTN An acronym for public switched telephone network, which is the traditional analog-based telephone system used in the United States that was originally designed for voice transmissions.
Public Key A special code, available in the public domain, that can be used to code and decode messages.
Pulse Code Modulation (PCM) A coding technique used to convert analog signals to digital signals and vice versa.
PVC An acronym for permanent virtual circuit, which is a communications channel that provides a logical connection between two sites instead of a physical one. In a connection- oriented protocol such as frame relay, PVCs appear as private links because a circuit must first be established between end nodes prior to data communications. The difference is PVCs are virtual circuits, not dedicated ones, and hence bandwidth is shared among multiple sites by multiplexing techniques. Thus, PVCs provide nondedicated connections through a shared medium, which enables data from multiple sites to be transmitted over the same link concurrently.
PVC Cable Any type of cable that contains an outer sheath or "jacket" that is composed of polyvinyl chloride (PVC). Also called non-plenum cable.
Quality of Service (QoS) Parameters associated with data prioritization that specify such things as the amount of bandwidth a priority data transmission requires as well as the maximum amount of latency the transmission can tolerate in order for the transmission to be meaningful. QoS is needed for transmitting real-time voice and video traffic.
Radio Frequencies (RF) A generic term used to describe a transmission method that uses electromagnetic waveforms.
Radio Transmission Refers to any wireless technique that uses radio frequencies (RF) to transmit information.
RADSL An acronym for rate-adaptive digital subscriber line, which is a DSL variant that provides transmission rates similar to ADSL. Transmission rates can be adjusted based on distance and line quality. Up to 7 Mbps downstream rate.
Random Access Protocol A network protocol that governs how nodes are to act in those instances where accessing a shared medium at will, on a first-come, first-served basis is permitted. Also called contention protocol.
RBOC An acronym for regional bell operating company, which refers to a regional telephone company in the United States formed after the AT&T breakup in 1984.
Redundancy Bits Extra bits incorporated into a data frame that provide error correction information. A data set composed of both user data and redundancy bits is called a codeword. Also called check bits.
Reliable Service A type of service that requires a sending node to acknowledge receipt of data. This is called an acknowledged datagram service.
Repeater A layer 1 device that provides both physical and electrical connections. Their function is to regenerate and propagate signals—they receive signals from one cable segment, regenerate, re-time, and amplify them, and then transmit these "revitalized" signals to another cable segment. Repeaters extend the diameter of Ethernet/802.3 networks but are considered to be part of the same collision domain.
RFC An acronym for request for comments, which are the working notes of the Internet research and development community. RFCs provide network researchers and designers a medium for documenting and sharing new ideas, network protocol concepts, and other technically-related information. They contain meeting notes from Internet organizations, describe various Internet protocols and experiments, and detail standards specifications. All Internet standards are published as RFCs (not all RFCs are Internet standards, though).
Ring Design A network design that is based on a broadcast topology in which nodes are connected to a physical ring, and data messages are transferred around the ring in either a clockwise or counterclockwise (or both) manner.
RIP An acronym for routing Internet protocol, a distance-vector algorithm that determines the best route by using a hops metric. RIP was at one time the de facto standard for IP routing.
RIP-2 An updated version of RIP, formally known as RIP version 2. New features include authentication, interpretation of IGP and BGP routes, subnet mask support, and multicasting support.
Risk Analysis The assessment of how much a loss is going to cost a company.
RJ A designation that refers to a specific series of connectors defined in the Universal Service Order Code (USOC) definitions of telephone circuits. "RJ" is telephone lingo for "registered jack."
RJ-11 A four-wire modular connector used for telephones.
RJ-45 An eight-wire modular connector used in 10BASE-T LANs.
Router A layer 3 device that is responsible for determining the appropriate path a packet takes to reach its destination. Commonly referred to as gateway.
Routing A layer 3 function that directs data packets from source to destination.
Routing Arbiter (RA) A project that facilitates the exchange of network traffic among various independent Internet backbones. Special servers that contain routing information databases of network routes are maintained so that the transfer of traffic among the various backbone providers meeting at a NAP is facilitated.
Routing Protocol A specific protocol that determines the route a packet should take from source to destination. Routing protocols are a function of network protocols. For example, if your network protocol is TCP/IP, then several routing protocol options are available including RIP, RIP-2, and OSPF. If your network protocol is OSI’s CNLP, then
your routing protocol is IS-IS. Routing protocols determine the "best" path a packet should take when it travels through a network from source to destination, and maintain routing tables that contain information about the network’s topology. Routing protocols rely on routing algorithms to calculate the least-cost path from source to destination.
Routing Table A data structure that contains, among others, the destination address of a node or network, known router addresses, and the network interface associated with a particular router address. When a router receives a packet it looks at the packet’s destination address to identify the destination network, searches its routing table for an entry corresponding to this destination, and then forwards the packet to the next router via the appropriate interface.
RSA An acronym for Rivest, Shamir, and Adleman, which are the last names of the three individuals who designed the RSA public-key encryption algorithm.
RSVP An acronym for resource reservation protocol, which is an layer 3 protocol developed by IETF to provide a mechanism to control network latency for specific applications. This is done by prioritizing data and allocating sufficient bandwidth for data transmission. RSVP can be thought of as an IP-based Quality of Service (QoS) protocol.
Runt Frame An Ethernet/802.3 frame that has at least 8 bytes but less than 64 bytes long and have a valid CRC checksum.
SAN An acronym for storage area network, which is a network dedicated exclusively for storing data.
Satellite Communication System An RF-based broadcast network design involving Earth ground stations and orbiting communication satellites. Data transmissions from a land-based antenna to the satellite (called the uplink) are generally point-to-point, but all nodes that are part of the network are able to receive the satellite’s downlink transmissions.
SC Connector A TIA/EIA-568A standard connector for fiber-optic cable; also called a 568SC connector.
SDH An acronym for synchronous digital hierarchy, which is an ITU-T physical layer standard that provides an international specification for high-speed digital transmission via optical fiber. SDH incorporates SONET and uses the STM signal hierarchy as its basic building block. SDH is essentially the same as SONET, and at OC-3 rates and higher, the two are virtually identical.
SDSL An acronym for symmetric digital subscriber line, which is a DSL variant in which traffic is transmitted at same rate in each direction. Maximum transmission rate is 768 kbps. Uses single-wire pair. Telephone service not supported. Suitable for videoconferencing.
Segmentation See partitioning.
Serial Communication A data transmission method in which the bits representing a character of data are transmitted in sequence, one bit at a time, over a single communications channel. (Also referred to as serial transmission.)
Server A networked device that provides resources to client machines. Examples include print servers, mail servers, file servers, and web servers. Servers are shared by more than user; clients have only a single user.
Shannon’s Limit A mathematical theorem, named for the mathematician who derived it, Claude Shannon, that describes a model for determining the maximum data rate of a
noisy, analog communications channel. Shannon’s Limit is given by the following formula, Maximum Data Rate (MDR) = H log2(1 + ), where MDR is given in bits per second, H = bandwidth in Hertz, and = a measure of the signal-to-noise ratio.
Shielded Twisted Pair (STP) Twisted pair cable in which individual wire pairs are shielded (i.e., protected from noise).
Signal-to-Noise Ratio (SNR) A measure of signal quality expressed in decibels (dB). It is the ratio of signal strength to background noise on a cable. More specifically, SNR is the ratio between the desired signal and the unwanted noise in a communications medium. In plain, late twentieth century English, it is a measure of how badly a line sucks.
Signal Quality Error (SQE) A signal generated by a transceiver and read by the controller of the host to which the transceiver is connected. In V2.0 Ethernet, SQE is called heartbeat and is generated periodically to inform the host’s controller that the transceiver is "alive." In IEEE 802,3, SQE is only generated when a real signal quality error occurs.
Simplex Communication A data transmission method in which data may flow in only one direction; one device assumes the role of sender and the other assumes the role of receiver. These roles are fixed and cannot be reversed. An example of a simplex communication is a television transmission.
Single-attachment Station (SAS) An FDDI node that is connected to only the primary pair of fibers and can be isolated from the network in the case of some types of failure A SAS is also called Class B node.
Single Mode Fiber A type of fiber-optic cable with a core diameter ranging from 7 µm to 9 µm. In single mode fiber, only a single ray of light, called the axial ray, can pass. Thus, a light wave entering the fiber exits with very little distortion, even at very long distances and very high data rates.
SIP An acronym for SMDS interface protocol, which consists of three protocol levels: SIP Level 3, SIP Level 2, and SIP Level 1. These three protocol levels are similar in function to the first three layers of the OSI model but represent SMDS’s MAC sublayer and hence operate at the data link layer.
SMA Connector A fiber-optic cable connector that meets military specifications.
Smart Card A type of "credit card" with embedded integrated circuits that store information in electronic form and used for authentication. Similar to a digital certificate.
SMDS An acronym for switched multimegabit data service, a cell-based, connectionless, high-speed, public, packet-switched, broadband, metropolitan area data network.
SOHO An acronym for small office/home office.
SONET An acronym for synchronous optical network, which is an ANSI physical layer standard that provides an international specification for high-speed digital transmission via optical fiber. At the source interface, signals are converted from electrical to optical form. They are then converted back to electrical form at the destination interface. The basic building block of the SONET signal hierarchy is STS-1 (51.84 Mbps).
Spanning Tree A single path between source and destination nodes that does not include any loops. It is a loop-free subset of a network’s topology. The spanning tree algorithm,
specified in IEEE 802.1d, describes how bridges (and switches) can communicate to avoid network loops.
SPID An acronym for service profile identification, which are numbers assigned by the telcos and used to identify the various processes of an ISDN device. (Used only in North America.)
Split-horizon A strategy employed by RIP to insure that a router never sends routing information back in the direction from which it came. Used to prevent routing loops.
Split-horizon With Poisoned Reverse A modified split-horizon strategy in which routing information provided by a neighbor is included in updates sent back to that neighbor. Such routes are assigned a cost factor of infinity, which makes the network unreachable.
Spread Spectrum A radio technology that refers to a security technique. Spread spectrum transmission camouflages data by mixing signals with a pseudonoise (PN) pattern and transmitting the real signal with the PN pattern. The transmission signal is spread over a range of the frequencies in radio spectrum.
Statistical Multiplexing A multiplexing technique that allocates part of a channel’s capacity only to those nodes that require it (i.e., have data to transmit). Based on the premise that, statistically, not all devices necessarily require a portion of the channel at exactly the same time.
Subnet Mask A special network address used to identify a specific subnetwork. Using a unique bit combination, a mask partitions an address into a network ID and a host ID.
Subnetting Refers to the partitioning of a network address space into separate, autonomous subnetworks. Key to subnetting is a network’s subnet mask.
Subnetwork Refers to a network segment. Commonly abbreviated as subnet.
SVC An acronym for switched virtual circuit, which is a circuit between source and destination nodes that is established on the fly and then removed after data communications have ended. SVCs are logical, dynamic connections instead of logical permanent connections as with PVCs. Thus, SVCs provide switched, on-demand connectivity.
Synchronous Communication A data communication method that requires sending and receiving nodes to monitor each other’s transmissions so that the receiving node always knows when a new character is being sent. In this instance, the sending and receiving nodes are "in synch" with each other.
Stackable Repeater Hub Individual repeater units "stacked" one on top of another. Instead of using a common shared backplane, stackable hubs use a "pseudo-backplane" based on a common connector interface. An external cable interconnects the individual hubs in a daisy-chained manner. Once interconnected, the entire chain of hubs becomes a single logical unit that functions as a single repeater.
Stacking Height The maximum number of stackable repeater hubs permitted.
Standby Monitor A station (i.e., node) on a token ring network that oversees the active monitor. Except for the active monitor, all token ring nodes are standby monitors.
Star A network configuration characterized by the presence of a central processing hub, which serves as a wire center for connecting nodes. All data must pass through the hub in order for nodes to communicate with each other.
Stateful Firewall A device or product that monitors all transactions between two systems and is capable of (1) identifying a specific condition in the transaction between two
applications, (2) predicting what should transpire next in the transaction, and (3) detecting when normal operational "states" of the connection are being violated.
Static Route A fixed route that is entered into a router’s routing table either manually or via a software configuration program.
ST Connector Similar to a BNC connector but used with fiber-optic cable.
Step-index Multimode Fiber A type of multimode fiber in which light pulses are guided along the cable from source to destination by reflecting off the cladding.
STM An acronym for synchronous transport module, which represents a digital transmission carrier system used for Synchronous Digital Hierarchy (SDH). STM rates range from STM-1, which is equivalent to OC-3 (155.52 Mbps) to STM-64, which is equivalent to OC-192 (9.953 Gbps).
Store-and-Forward A method used by bridges and switches in which the contents of an entire frame is captured by the device before a decision is made to filter or forward the frame. A store-and-forward network switch is also called a buffering switch. A network that based on this principle is called a store-and-forward network.
STS An acronym for synchronous transport signal, which is a digital transmission hierarchy used for SONET. STS rates range from STS-1, which is the equivalent of 28 DS-1 channels (51.84 Mbps) to STS-192, which is the equivalent of 5,376 DS-1 channels (9.953 Gbps). STS rates are the electrical equivalent of OC rates.
Switch A network device that filters or forwards data based on specific information. A layer 2 switch (e.g., an Ethernet switch), filters or forwards frames from one node to another using Mac-level (i.e., hardware) addresses; a layer 3 switch filters or forwards packets based on network addresses; and layer 4 (or higher) switches filter or forward messages based on specific application protocols. Forwarding rates are usually done at wire speed and via "private" connections, i.e., no other node "sees" the traffic. Switches partition Ethernet/802.3 networks into multiple collision domains.
Switched Ethernet An Ethernet/802.3 LAN that is based on network switches instead of repeaters or bridges. A switched Ethernet LAN isolates network traffic between sending and receiving nodes from all other connected nodes. It also transforms traditional Ethernet/802.3 from a broadcast technology to a point-to-point technology.
T1 Describes the multiplexing of 24 separate voice channels, each rated at 64 kbps, plus one 8 kbps framing channel, into a single, wideband digital signal rated at 1.544 Mbps.
T2 A multiplexed circuit that combines four T1 circuits and has an aggregate bandwidth of 6.312 Mbps.
T3 A multiplexed circuit that combines 28 T1 circuits and has an aggregate bandwidth of 44.736 Mbps.
T4 A multiplexed circuit that combines 168 T1 circuits and has an aggregate bandwidth of 274.176 Mbps.
TCP An acronym for transmission control protocol, which is a layer 4 connection-oriented protocol that performs several functions, including: providing for reliable transmission of data by furnishing end-to-end error detection and correction; guaranteeing that data are transferred across a network accurately and in the proper sequence; retransmitting any data not received by the destination node; and guaranteeing against data duplication between sending and receiving nodes. It is the "TCP" of TCP/IP.
TCP/IP An acronym for transmission control protocol/Internet protocol. Refers to a formal network protocol suite based on its two namesake sub-protocols, TCP and IP.
TE An acronym for terminal equipment, which represents a specific communication device that connects to an ISDN network. Two TEs are referenced in the specification: TE1 refers to an ISDN-compatible device (e.g., digital telephone or a computer with a built-in ISDN port), and TE2 refers to a non-compatible ISDN device (e.g., an analog telephone or a computer without a built-in ISDN port).
Telco An acronym for telephone company.
Terminal Adapter (TA) A device that connects non-compatible ISDN devices to an ISDN network. If a TA is used for an ISDN dialup connection, then it can be thought of as a modem. If a TA is used to connect a device to a LAN, then it can be thought of as a network interface card. It should be noted that although a TA is frequently referred to as an ISDN modem or digital modem in the context of an ISDN dialup connection, this reference is incorrect. By definition, a modem performs analog-to-digital and digital-to-analog conversions. Since ISDN is completely digital, no such conversions are necessary, which makes the expressions, ISDN modem or digital modem, incongruous.
Terminator Layer 1 device that prevents signal reflections by providing electrical resistance at the end of a cable to "absorb" signals to keep them from bouncing back and being heard again by the devices connected to the cable.
Thick Ethernet Describes IEEE 802.3 10BASE5, which uses "thick" coaxial cable (outer diameter between 0.375-inch and 0.405-inch) as its physical medium.
Thin Ethernet Describes IEEE 802.3 10BASE2, which uses "thin" coaxial cable (outer diameter between 0.175-inch and 0.195-inch) as its physical medium.
Threat Assessment An activity that involves determining how much security is necessary for proper control of system and network assets. Threat assessment is guided by answering the overriding question, "What assets are critical to the operation of my network and who do I think would want access to them?"
Throughput A realistic measure of the amount of data transmitted between two nodes in a given time period. It is a function of hardware/software speed, CPU power, overhead, and many other items. Compared to bandwidth, throughput is what the channel really achieves, where bandwidth is what is theoretically possible.
Time Division Multiplexing (TDM) A multiplexing technique that assigns to each node connected to a channel an identification number and a small amount of time in which to transmit. TDM-based transmissions are serially sequenced.
Token A special frame on a token ring or token bus network. Possession of the token permits a node to transmit data.
Token Bus A local area network technology based on a token-passing protocol for media access. Defined in IEEE 802.4. A token bus network is characterized as a logical ring on a physical bus—physically, the network resembles a bus topology, but logically, the network is arranged as a ring with respect to passing the token from node to node.
Token Passing Protocol A network protocol that requires nodes to first possess a special frame, called a token, prior to transmitting data. Token-passing schemes are both contention-free and collision-free.
Token Ring A local area network technology based on a token-passing protocol for media access control. Defined by IEEE 802.5. A token ring LAN is implemented either as
a logical ring using a physical ring topology, or as a logical ring structure arranged in a physical star configuration.
traceroute A unix program that depicts the gateways a packet transverses. A corresponding Microsoft NT command is called tracert.
Transceiver A service used in Ethernet/802.3 networks to connect nodes to the physical medium. Transceivers serve as both the physical connection and the electrical interface between a node and the physical medium, enabling the node to communicate with the medium. Transceivers transmit and receive signals simultaneously.
Tree A network configuration in which nodes are connected to one another in a hierarchical fashion. A root node or hub is connected to second level nodes or hubs; second- level devices are connected to third-level devices, which in turn are connected to fourth- level devices, and so forth.
Triple DES A variant of DES that uses three DES operations instead of one.
Tunneling See encapsulation.
Twisted Pair Cable A type of copper cable that uses at least two insulated copper wires that have been twisted together. There are two basic type: unshielded twisted pair (UTP) and shielded twisted pair (STP).
UDP An acronym for user datagram protocol, which is a connectionless protocol providing an unreliable datagram service. UDP does not furnish any end-to-end error detection or correction, and it does not retransmit any data it did not receive.
UDSL An acronym for universal digital subscriber line, which is a DSL variant that provides symmetrical service at 2 Mbps each way.
UNI An acronym for user-to-network interface, which is an end node’s port where the local loop terminates at a customer’s site.
Unicast A data transmission that is destined to a single recipient.
Unreliable Service A network service type that requires no acknowledgment of receipt of data from the receiving node to the sending node. This is called a datagram service.
Unshielded Twisted Pair (UTP) Twisted pair cable in which individual wire pairs are not shielded (i.e., protected from noise).
Utilization A network performance measure that specifies the amount of time a LAN spends successfully transmitting data. Average utilization means that over some period of time (e.g., a 10-hour period), on average, a certain percent of the LAN’s capacity is used for successfully transmitting data. Peak utilization means that at a specific moment in time, a certain percent of the LAN’s capacity was utilized.
V.22 bis ITU-T standard for 2400 bps full-duplex modems; cycles to 1200 bps/600 bps.
V.29 ITU-T standard for 9600 bps facsimile service.
V.32 ITU-T standard for 9600 bps modems; cycles to 4800 bps when line quality degrades, and cycles forward when line quality improves.
V.32 bis ITU-T standard that extends V.32 to 7200, 12,000, and 14,400 bps; cycles to lower rate when line quality degrades; cycles forward when line quality improves.
V.32 ter Pseudo-standard that extends V.32 bis to 19,200 bps and 21,600 bps.
V.34 ITU-T standard for 28,800 bps modems. (Note: V.34 modems upgraded with special software can achieve data rates of 31,200 bps or 33,600 bps.)
V.FAST Proprietary, pseudo-standard from Hayes and Rockwell for modems transmitting at data rates up to 28,800 bps; served as a migration path for V.34
V.42 ITU-T standard for modem error correction. Uses LAPM as the primary error-correcting protocol, with MNP classes 1 through 4 as an alternative.
V.42 bis ITU-T standard that enhances V.42 by incorporating the British Telecom Lempel Ziv data compression technique to V.42 error correction. Most V.32, V.32 bis, and V.34 compliant modems come with V.42 or V.42 bis or MNP.
V.90 ITU-T standard for 57,600 bps modems (commonly called "56K modems") in which asymmetric data rates apply (i.e., the send and receive rates are different). Depending on telephone line conditions, upstream rates (send) are restricted to 33,600 bps, and downstream rates (receive) are restricted to 57,600 bps. V.90 modems are designed for connections that are digital at one end and have involve only two analog-digital conversions each way.
vBNS An acronym for very high speed backbone network service, which is another National Science Foundation-funded research and educational network. The vBNS is a nationwide backbone network that currently operates at 622 Mbps (OC-12) and is accessible to only those involved in high-bandwidth research activities. The backbone is expected to be upgraded to OC-48 (2.488 Gbps) in 1999.
VDSL An acronym for very high-speed digital subscriber line, which is a DSL variant that provide asymmetric service over fiber. Downstream rates range from 13 Mbps to 52 Mbps; upstream rates range from 1.5 Mbps to 2.3 Mbps. Suitable for Internet/intranet access, video-on-demand, database access, remote LAN access, and high-definition TV.
Virtual Channel Connection (VCC) A virtual circuit that provides a logical connection between an ATM source and destination. Data can only be transmitted in one direction via a VCC. A VCC is denoted by a virtual channel identifier (VCI), which is included as part of the ATM cell header. Multiple virtual channels that share the same connection can be packaged into a single virtual path.
Virtual Channel Identifier (VCI) A parameter used to identify ATM virtual channels. VCI information is carried within an ATM cell header.
Virtual Circuit A nondedicated connection through a shared medium that gives the high- level user the appearance of a dedicated, direct connection from the source node to the destination node.
Virtual Path Connection (VPC) A semi-permanent connection that provides a logical collection of ATM virtual channels that have the same end points. More specifically, a VPC carries a group of virtual channels all of which have the same end points. Virtual paths enable any connection that uses the same network path from source to destination to be bundled into a single unit. A virtual path identifier (VPI) is used denote a virtual path and is included in a cell’s header. A virtual path can also provide a form of traffic control by logically (not physically) partitioning network traffic based on the type of data being carried and associated quality of service.
Virtual Path Identifier (VPI) A parameter used to identify ATM virtual path. VPI information is carried within an ATM cell header.
VLAN An acronym for "virtual local area network." Nodes comprising a VLAN are not physically connected to the same medium. Instead, they are connected in a virtual sense using specially designed software that groups several ports in a switch into a single work
group. Nodes connected to these ports are considered to be part of a workgroup, and network traffic from any node/port is (usually) limited to only those nodes or ports assigned to the workgroup.
VOFR An acronym for voice over frame relay, which refers to transmitting voice signals over a frame relay network.
Voice Over IP (VOIP) A technology that enables users to place telephone calls across the Internet.
VPN An acronym for virtual private network, which refers to an IP connection between two sites over a public IP network that has its payload traffic encrypted so that only source and destination nodes can decrypt the traffic packets. A VPN enables a publicly accessible network to be used for highly confidential, dynamic, and secure data transmissions.
WAN An acronym for wide are network, which interconnects computing resources that are widely separated geographically (usually over 100 km). This includes towns, cities, states, and countries. A WAN generally spans an area greater than five miles (eight kilometers). A WAN can be thought of as consisting of a collection of LANs.
Wavelength A measure of the length of a wave. It is the distance an electrical or light signal travels in one complete cycle.
Wavelength Division Multiplexing (WDM) A multiplexing method used with fiber- optic cables. Involves the simultaneous transmission of light sources over a single fiber- optic channel. Light sources of different wavelengths are combined by a WDM multiplexer and transmitted over a single line. When the signals arrive, a WDM demultiplexer separates them and transmits them to their respective destination receivers.
Wire A general term used to describe the physical layer of a network. The three main physical attributes of wire are conductor, insulation, and outer jacket. Wire also has three important electrical characteristics that can directly affect the quality of the signal transmitted across it: capacitance, impedance, and attenuation. Signal quality is affected most by the combination of attenuation and capacitance. The two primary forms of wire are copper and fiber. Also called cable.
Wireless Communications A type of communications in which signals travel through space instead of through a physical cable. There are two general types of wireless communication: radio transmission and infrared transmission.
Wire Speed A unit of measure used to describe a device’s maximum (i.e., fastest) filtering and forwarding rates. In Ethernet/802.3, wire speed is equal to 14,880 frames per second. This is frequently reported as 14,880 packets per second. (See Box 8-3.)
WLAN An acronym for wireless LAN.
Workgroup Switch A term used to describe one application of an Ethernet switch. A workgroup switch partitions a single, shared medium into multiple, shared media and supports more than MAC address per port. Also called segment switches.
Workstation A computer system that has its own operating system and is connected to a network. A workstation can be a personal computer such as a Macintosh or Intel-based PC, a graphics workstation such as those manufactured by Sun Microsystems, a super- minicomputer such as IBM’s AS/400, a super-microcomputer such as DEC’s Alpha, or a mainframe such as an IBM ES-9000. Also called host, server, desktop, or client.
Converted to .html by Kevin Manson
Feb 9,2000
Please report conversion errors
to:
mailto:cybercop@mindspring.com